Threat-informed defense with LimaCharlie and FourCore ATTACK

Attackers evolve fast and we need to do upskill our defenses and teams against them. Adversary Emulation is a way to mimic threats and build evidence of detection and response against threats. We are able to track the coverage and detections against potential threats in our environment.
If you take a pentest and followe a specific threat-actor's tactics, techniques and procedures, that is emulation of the threat. There are various tools and projects to simulate cyber attacks. In this blog, we will use the FourCore ATTACK platform to emulate threats and LimaCharlie to build a detection infrastructure.
Our goal is to make offensive security accessible and continuous - helping security teams, red and blue alike, of all skill levels to be armed with expert capability and collaborate proactively to protect against the most imminent threats.
Using FourCore ATTACK
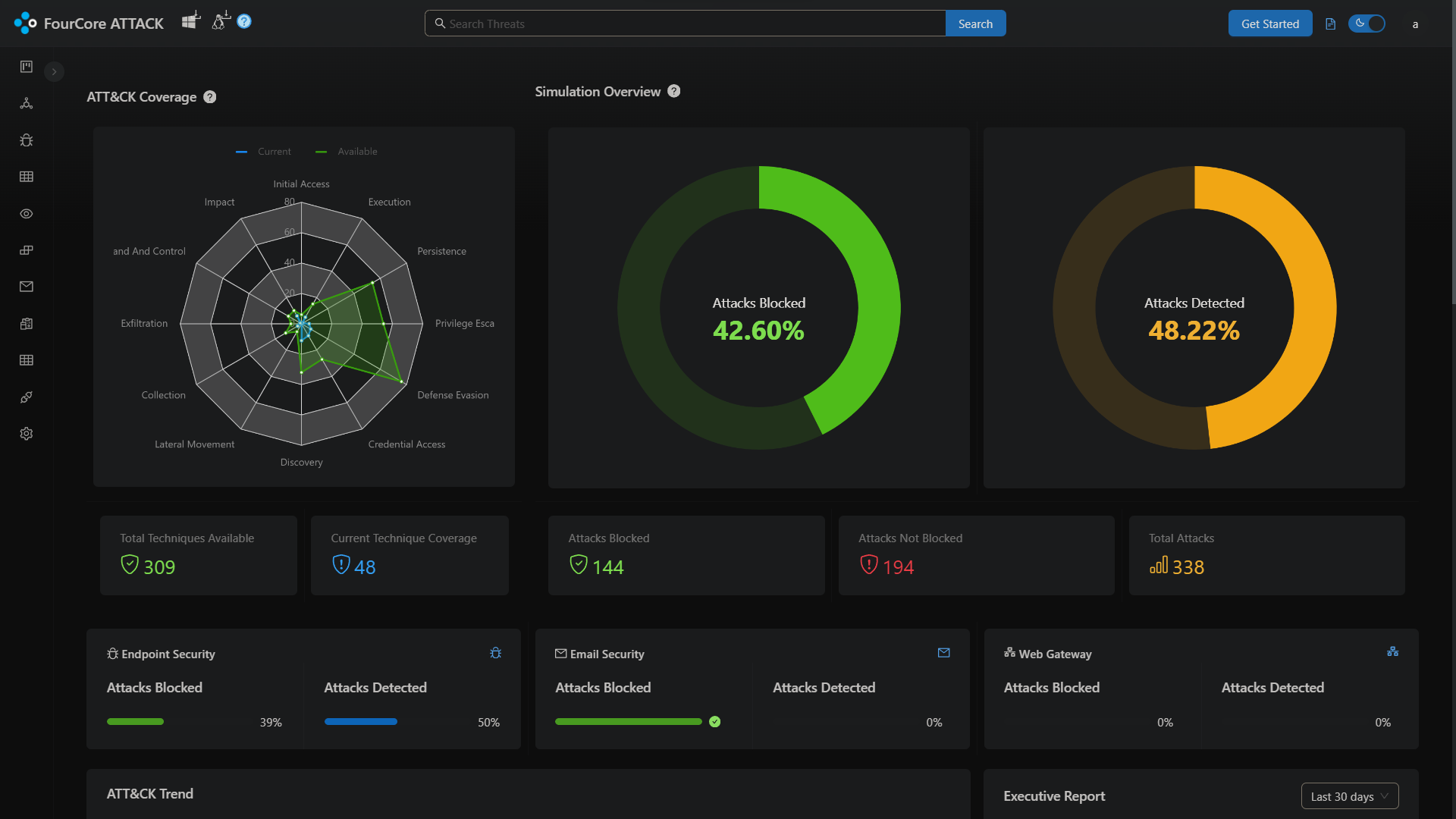
We have set up our account on the FourCore ATTACK cloud platform, and we'll get started by deploying the agent on our target system. You can deploy agents on Windows and Linux systems for simulating threats.
This system is a Cloud Machine running Windows Server 2016 with the LimaCharlie agent to collect telemetry. We will use the ATTACK Agent Powershell script to deploy the agent on our system "4C-16-AGENT" running Windows Server 2016.
Attack Library
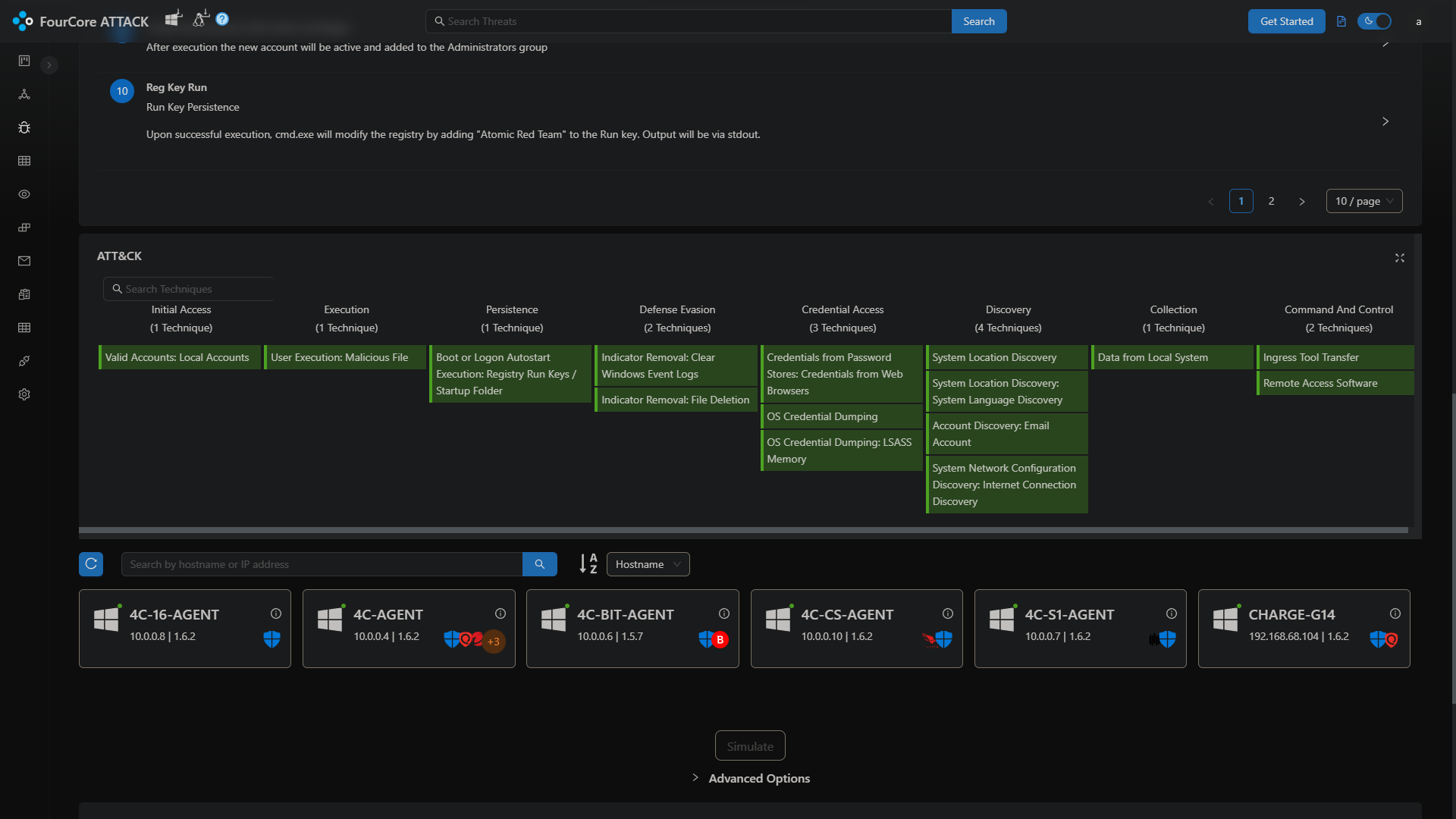
We can explore the attacks on the platform from the Attack Library. All attack chains and actions on the platform are tagged with MITRE ATT&CK®️ techniques, you can also filter attack by techniques, supported platforms and categories. Let's search for the Qakbot attack chain to emulate on 4C-16-AGENT, we'll hunt and detect for the same threat in LimaCharlie.
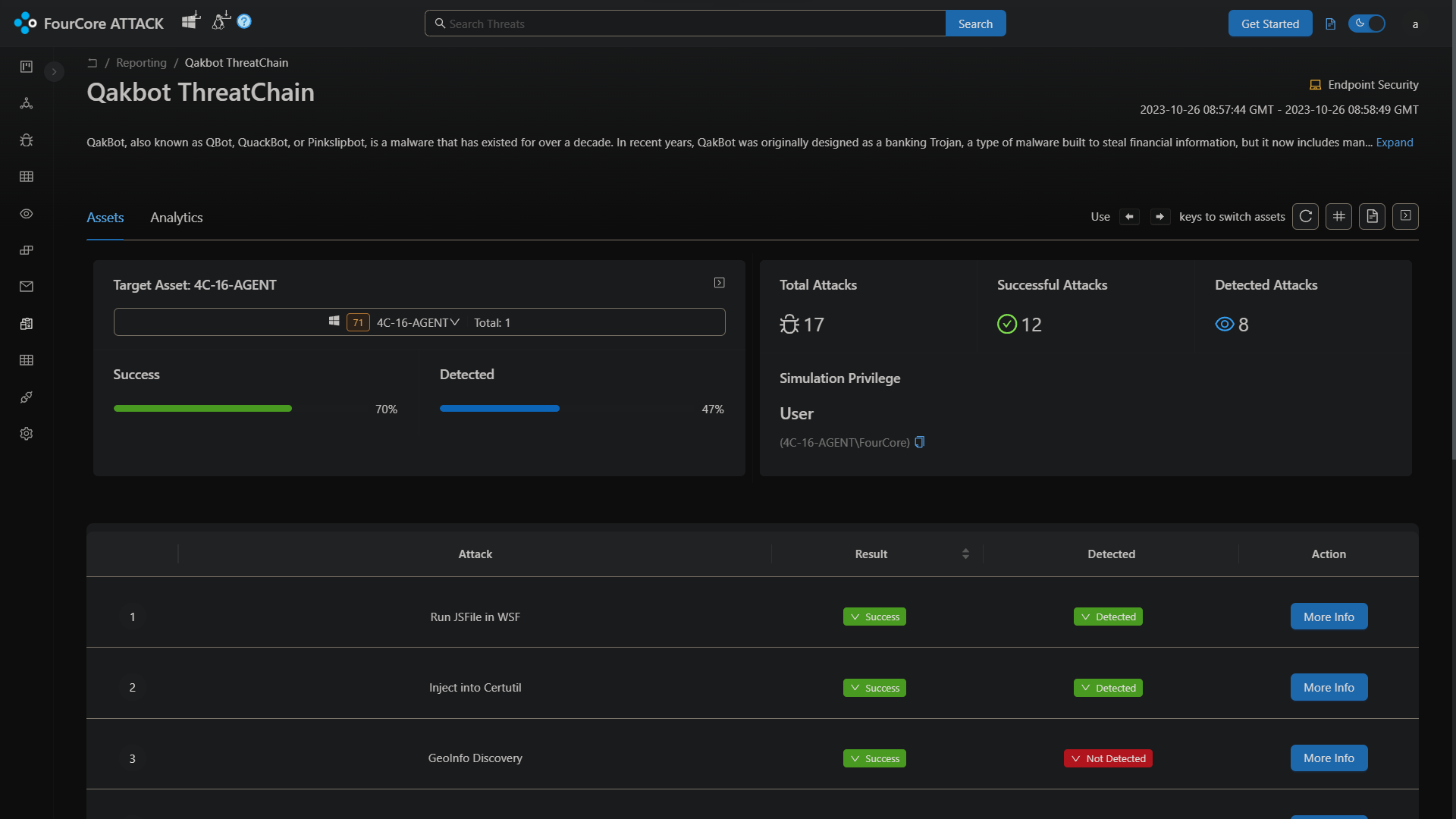
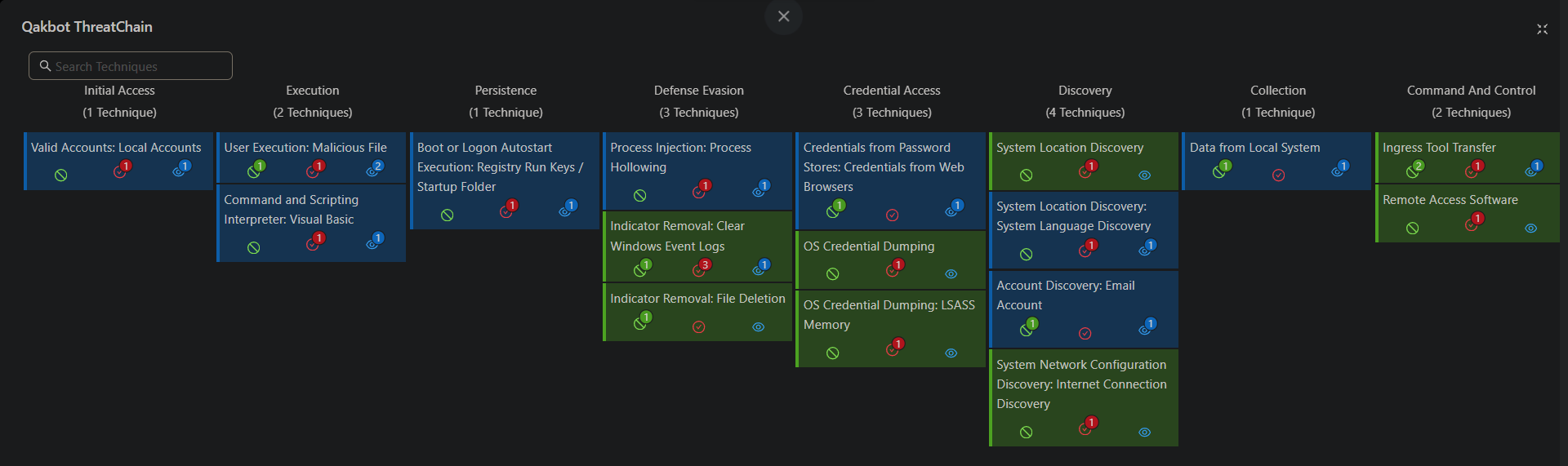
Qakbot Threat Emulation
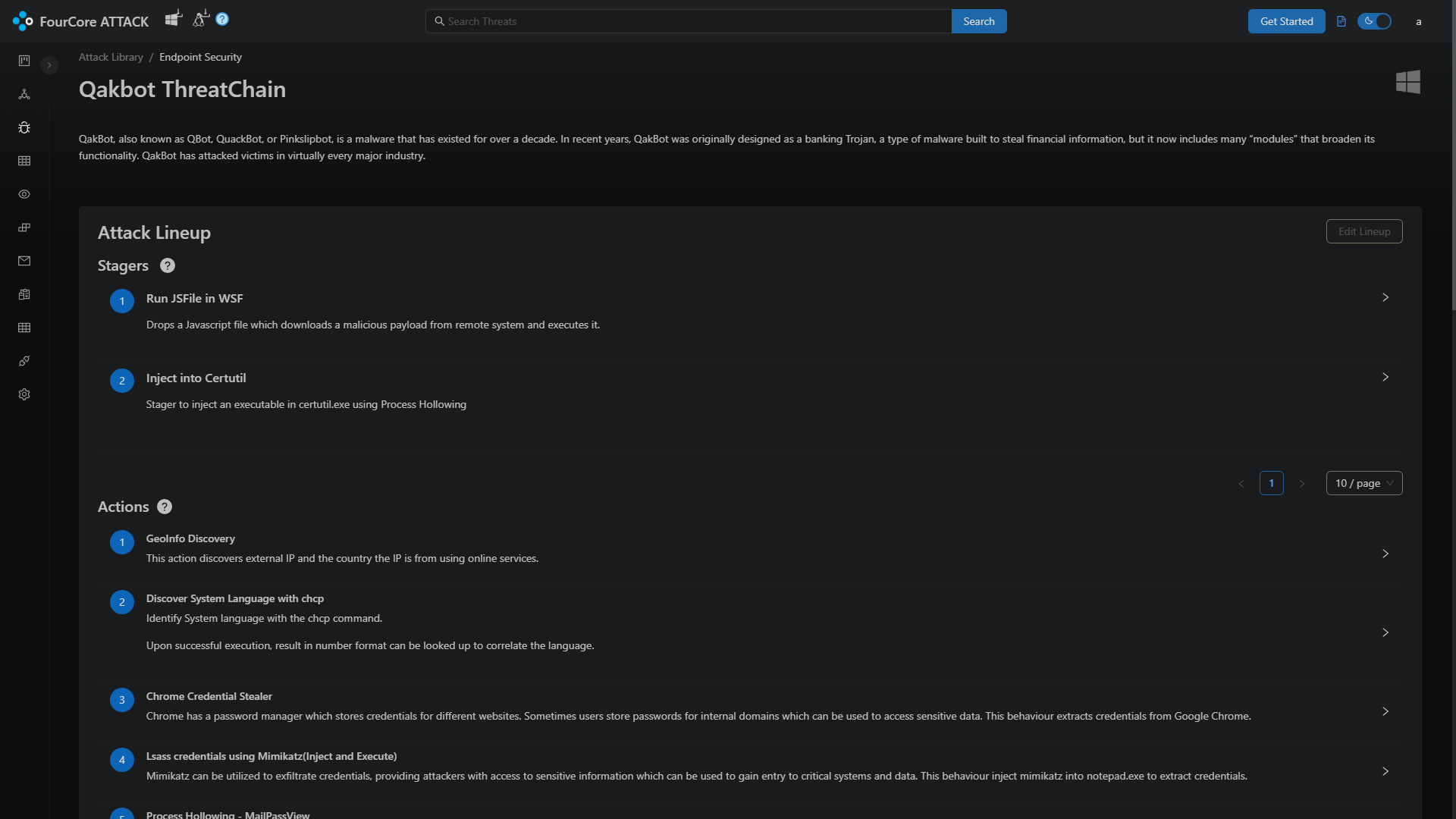
We'll emulate the Qakbot attack chain on 4C-16-AGENT. Every time a simulation is launched, the platform generates a dynamic payload which is delivered by the agent on the target system. This is core to the assumed breach methodology implemented by the FourCore ATTACK platform to emulate threats realistically.
The Qakbot attack chain implements a multi-stage attack which starts from a wsf script containing javascript which launches a DLL using rundll32.exe, if the wsf script is successful, the DLL payload will further spawn certutil.exe and utilize the "Process Hollowing" technique to execute the final payload inside certutil.exe. If these stagers are successful, the payload will execute various actions associated with operators using Qakbot.
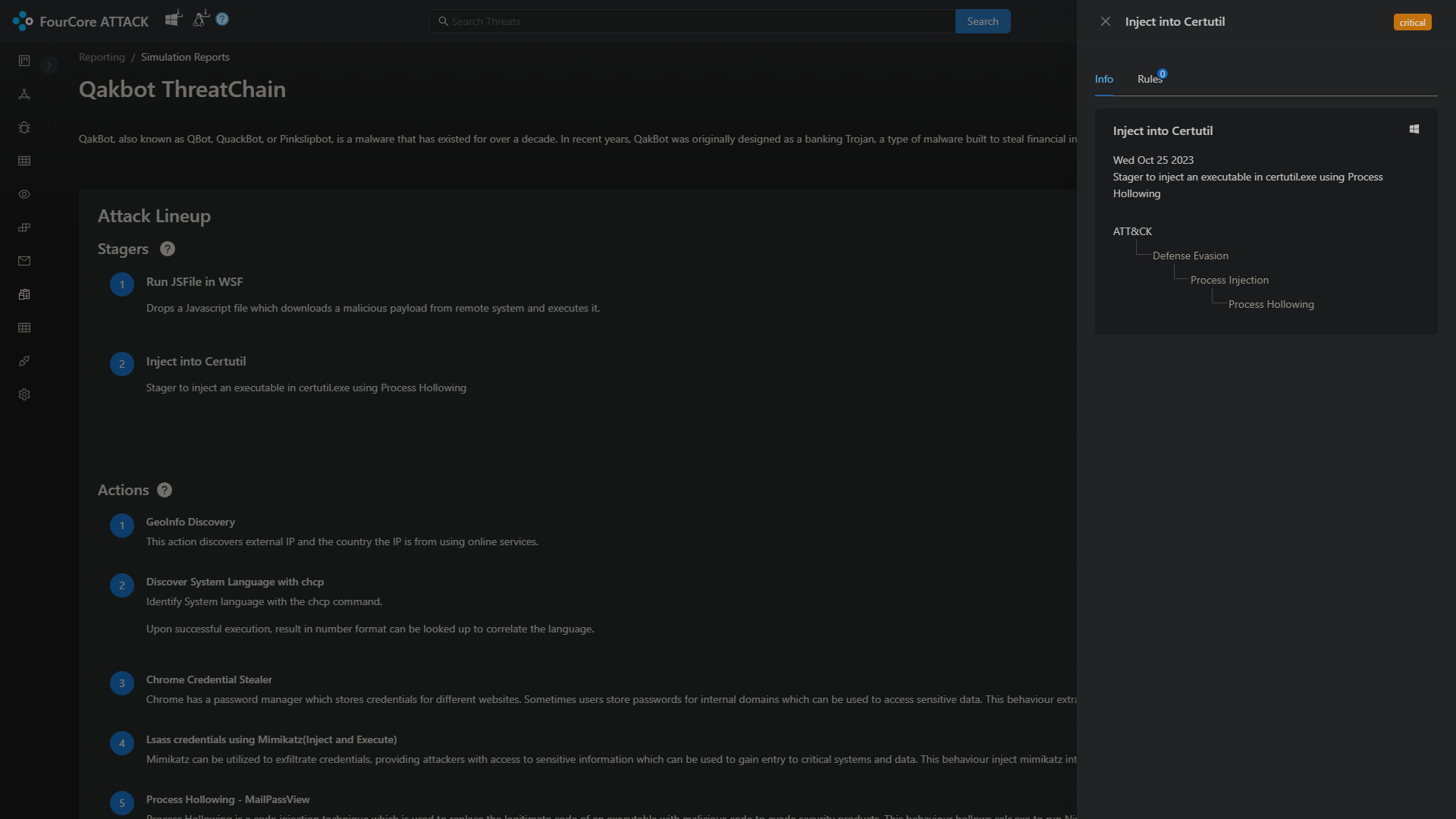
Every action and stager reports back it's status, logs, IoCs, outputs and any files to be collected back to the platform, these logs are valuable in understanding what happened during the attack, making it trivial to correlate attacks with security tools and finding detection opportunities.
Using LimaCharlie
Limacharlie SecOps Cloud Platform is a security operations platform which can power a complete SOC with the flexibility as you require. It's a unified and open platform to build detection and response pipelines for your environments, be it on endpoints, cloud or anywhere else.
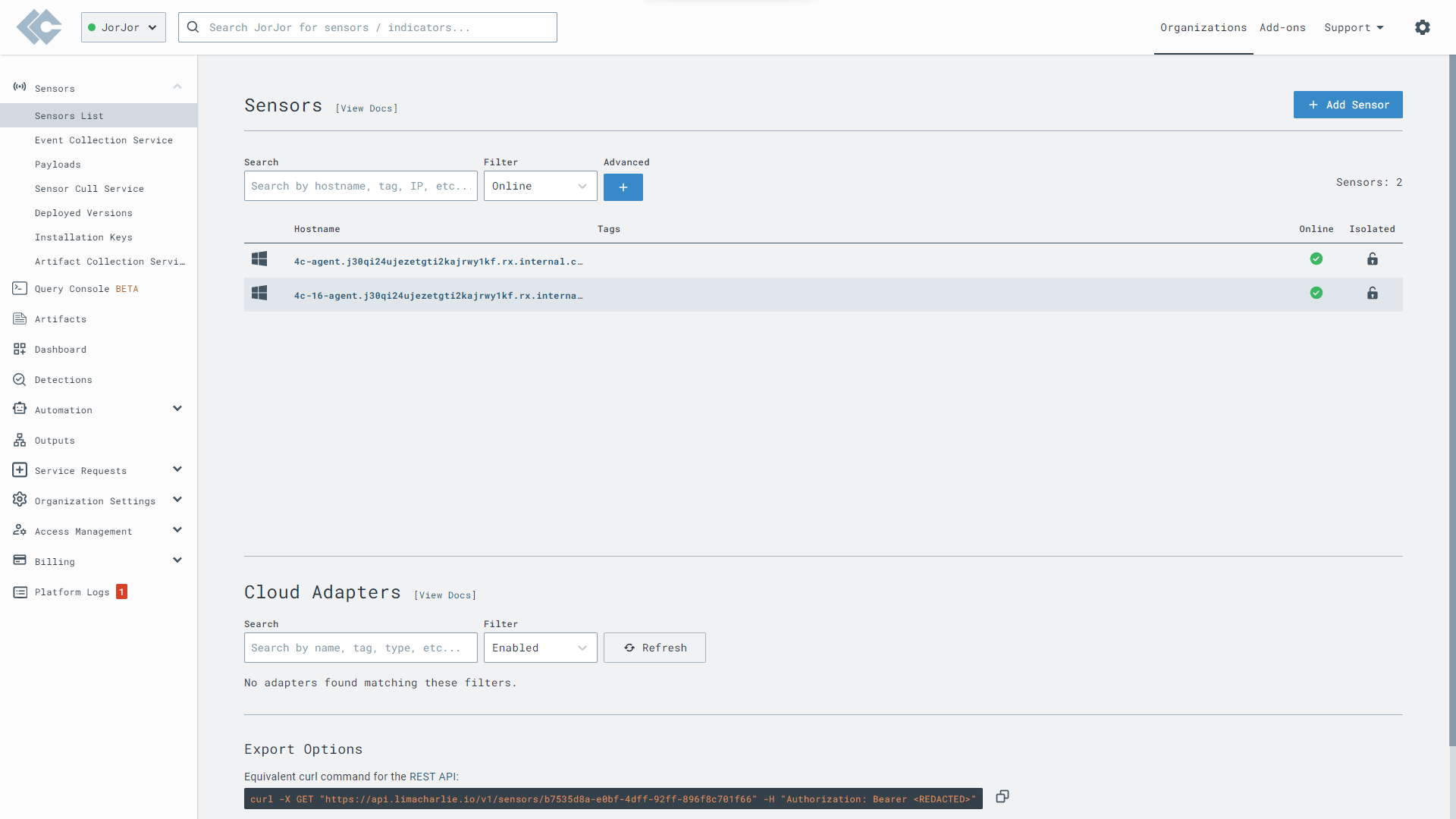
We have deployed the LimaCharlie endpoint sensor on 4C-16-AGENT, the agent will collect telemetry from the endpoint and the platform will run detection rules on these logs.
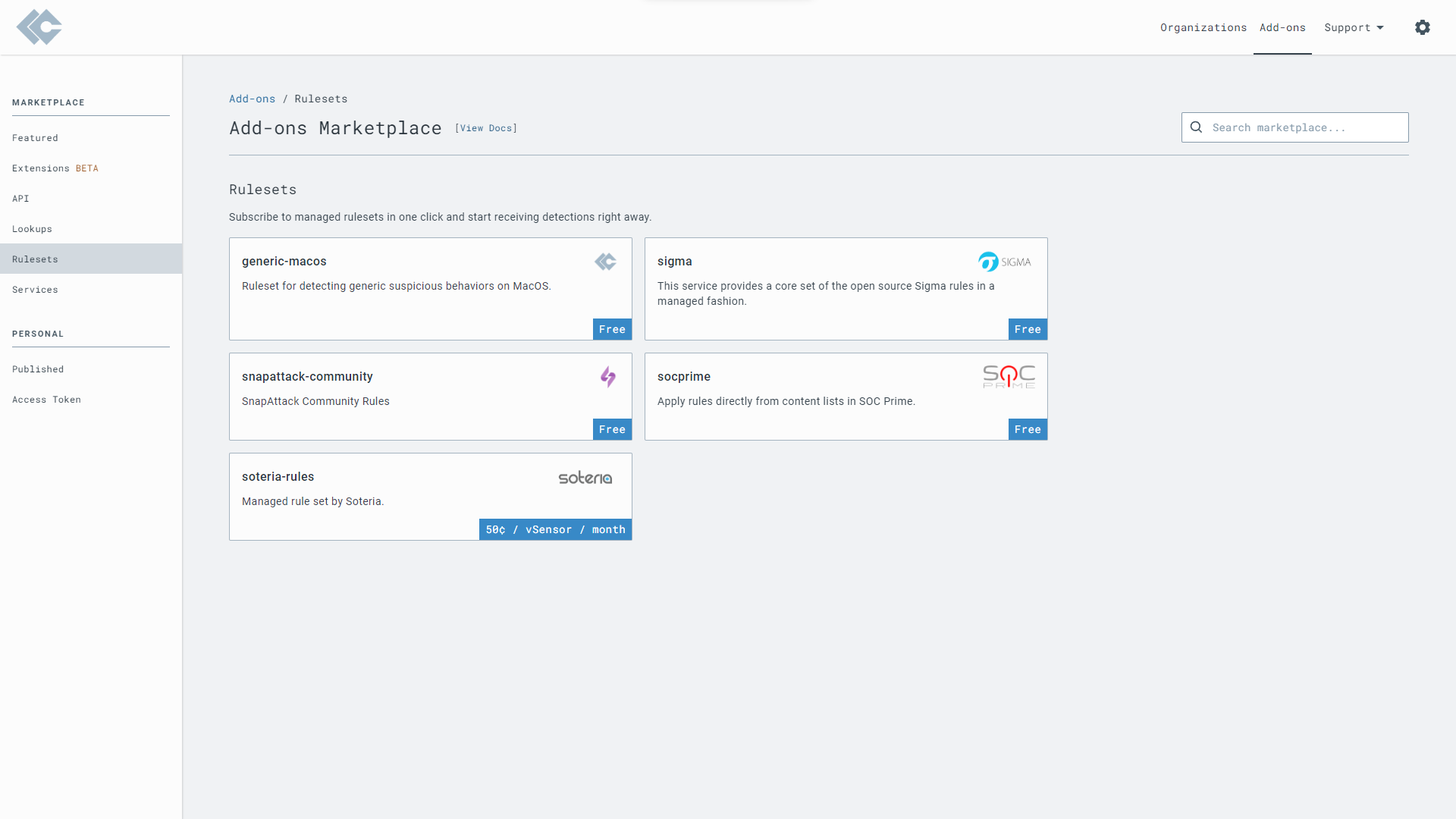
The LimaCharlie platform allows various add-ons to bring functionality such as VirusTotal enrichment, detection rules and more. We have enabled Soteria, Snapattack Community and Sigma rules on our account by default, this brings a large amount of default rules to detect various threats.
Integrating LimaCharlie with FourCore ATTACK
Navigate to the integrations dashboard on FourCore ATTACK and open the LimaCharlie integration configuration. We require our LimaCharlie OID and API Key to access the LimaCharlie API.
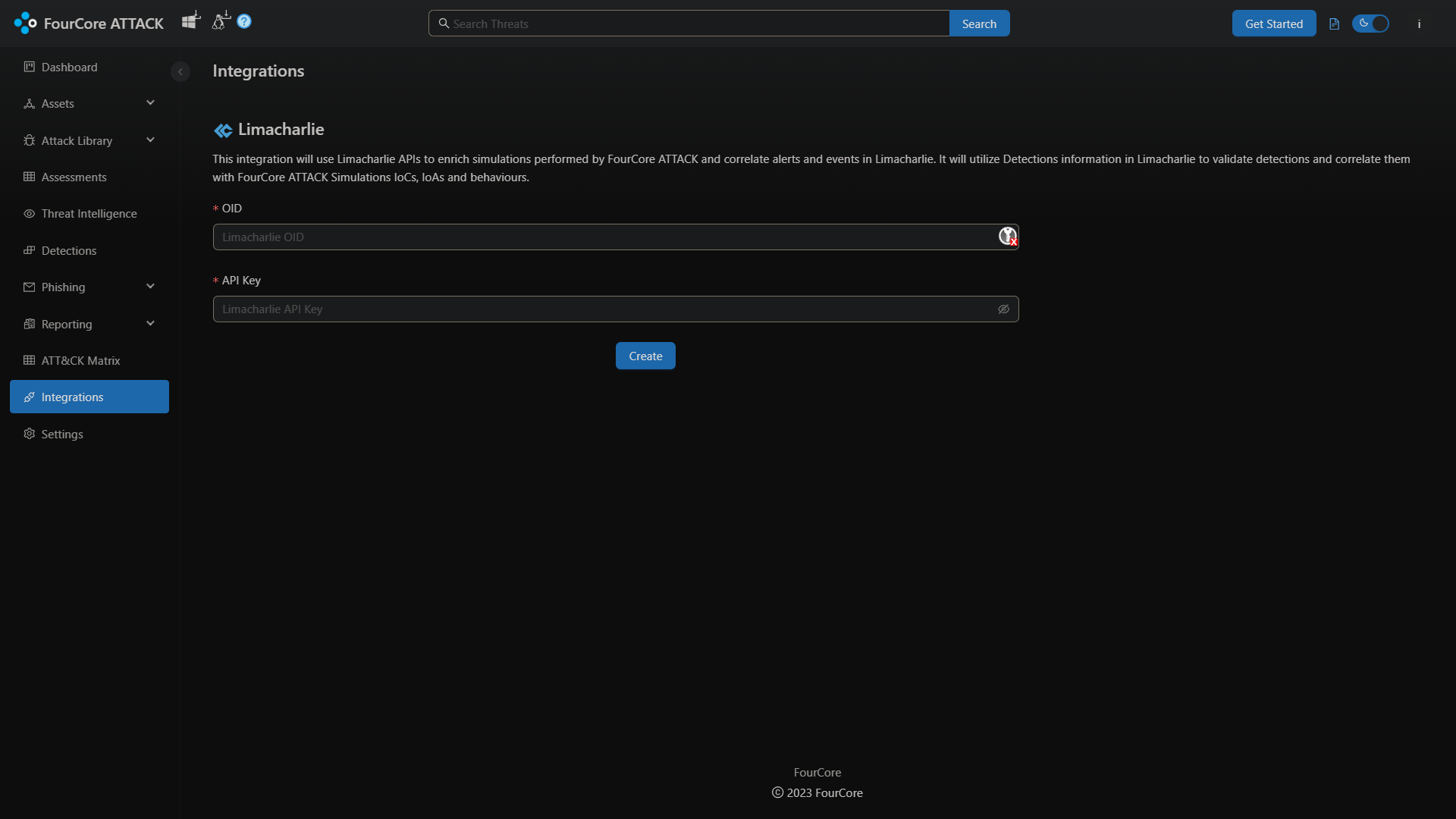
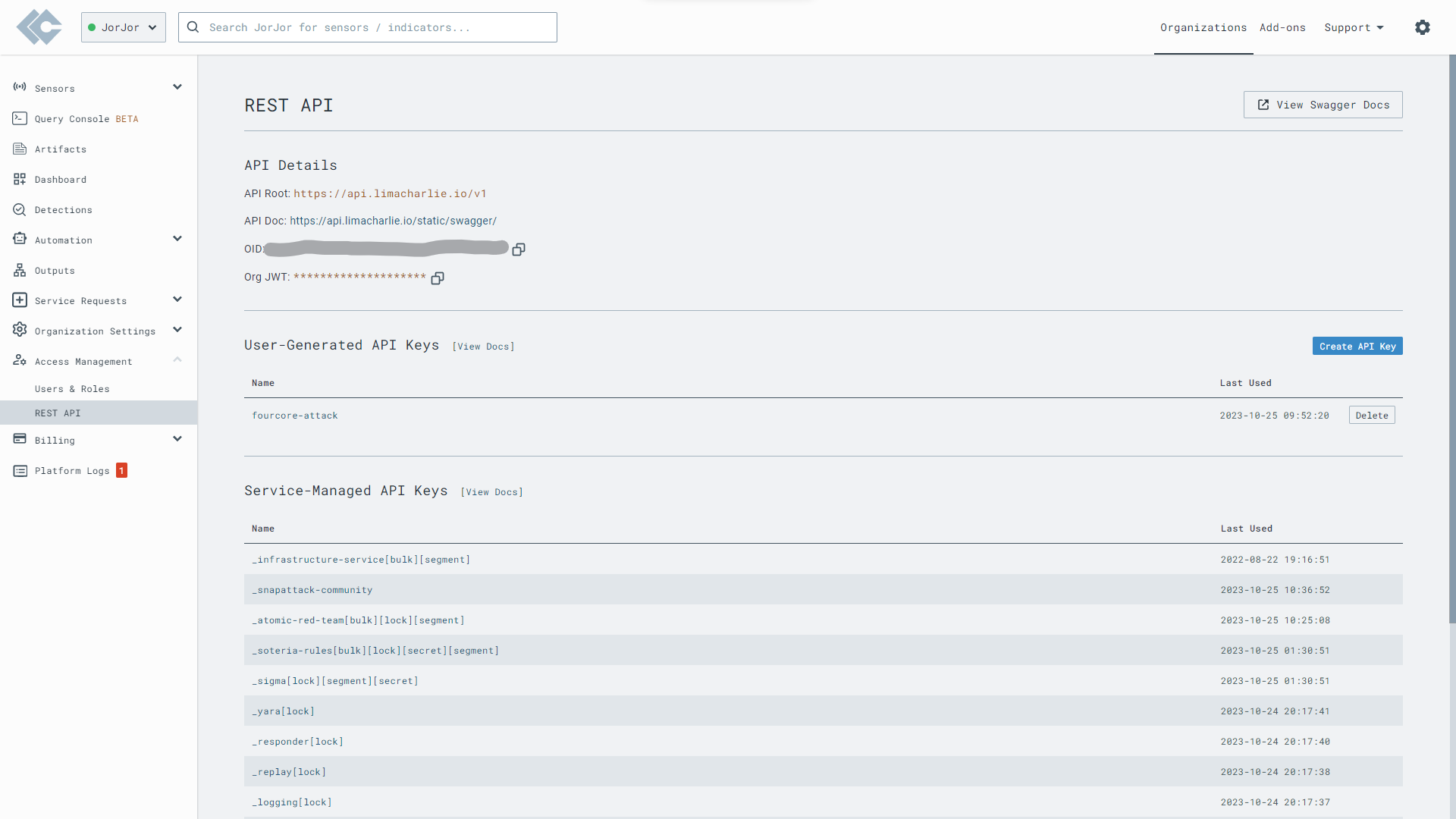
We can get the LimaCharlie OID and API Key from the Access Management -> REST API page. Generate new "User-Generated API Key" and we have named it "fourcore-attack". Copy the OID, the generated API Key and save it on the FourCore ATTACK Dashboard.
Any further attacks will be correlated for detections that occurred in LimaCharlie. This correlation happens using the IOC information reported by the attacks and stagers leading to an accurate automated correlation. The IoCs can also be used to manually correlate these executions.
Hunting Qakbot
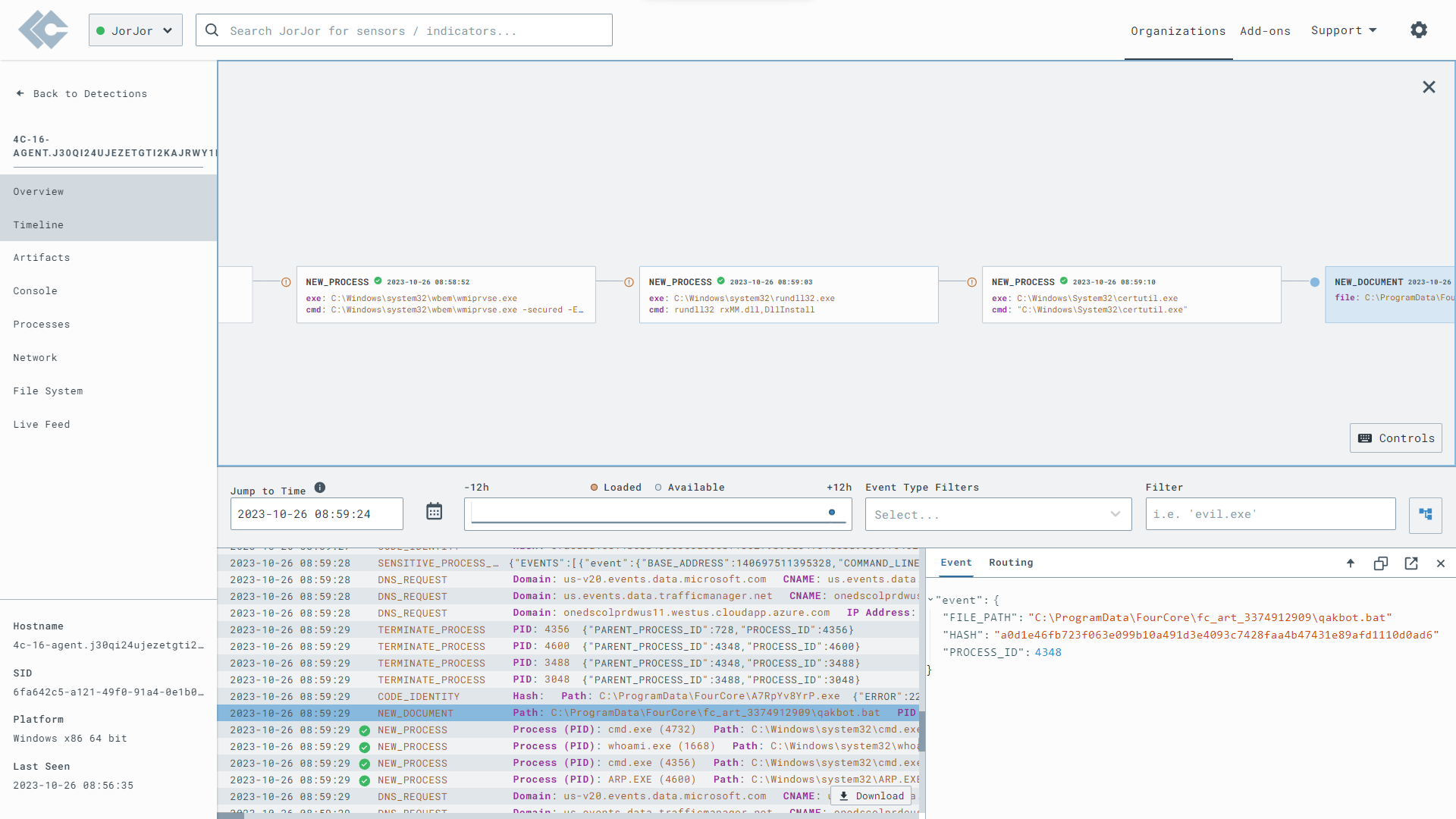
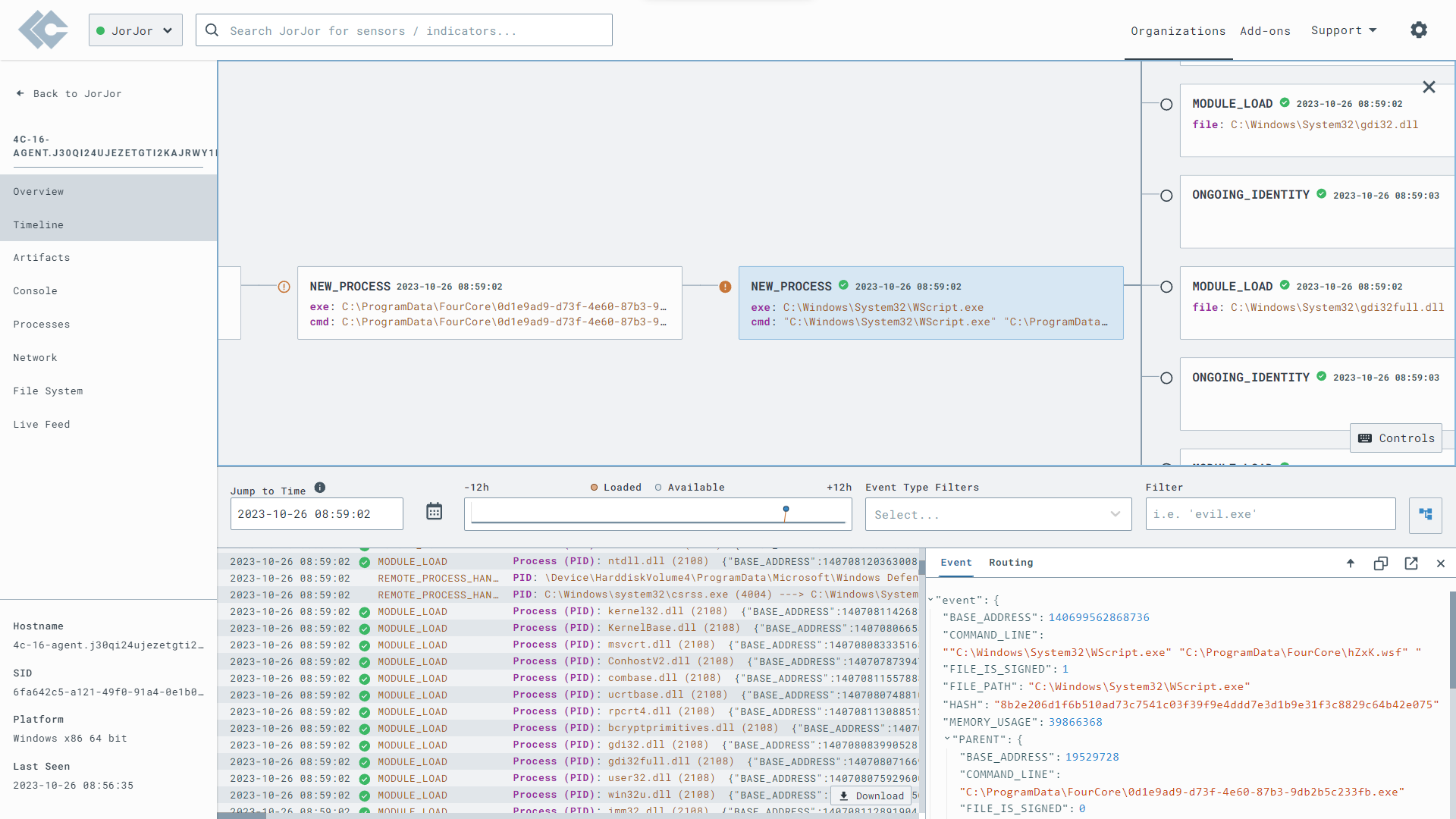
The Qakbot attack chain is a multi-stage attack as we described above. The rulesets we enabled in LimaCharlie led to many successful detections of the stagers and payloads involved in the attack c hain. In the below screenshot, we can see the process tree for the stagers from telemetry collected by the LimaCharlie agent.
In the FourCore ATTACK Platform, we can see the associated IoCs, Outputs generated by the payloads and Alerts correlated with the LimaCharlie API integration.
WSF Execution
The WSF script is generated by the implant, written to disk and executed. This script contains a job to execute jscript code for downloading the next stage payload DLL, and using rundll32.exe to execute the payload. This is one of the initial access techniques that Qakbot operators utilize and mutate often.
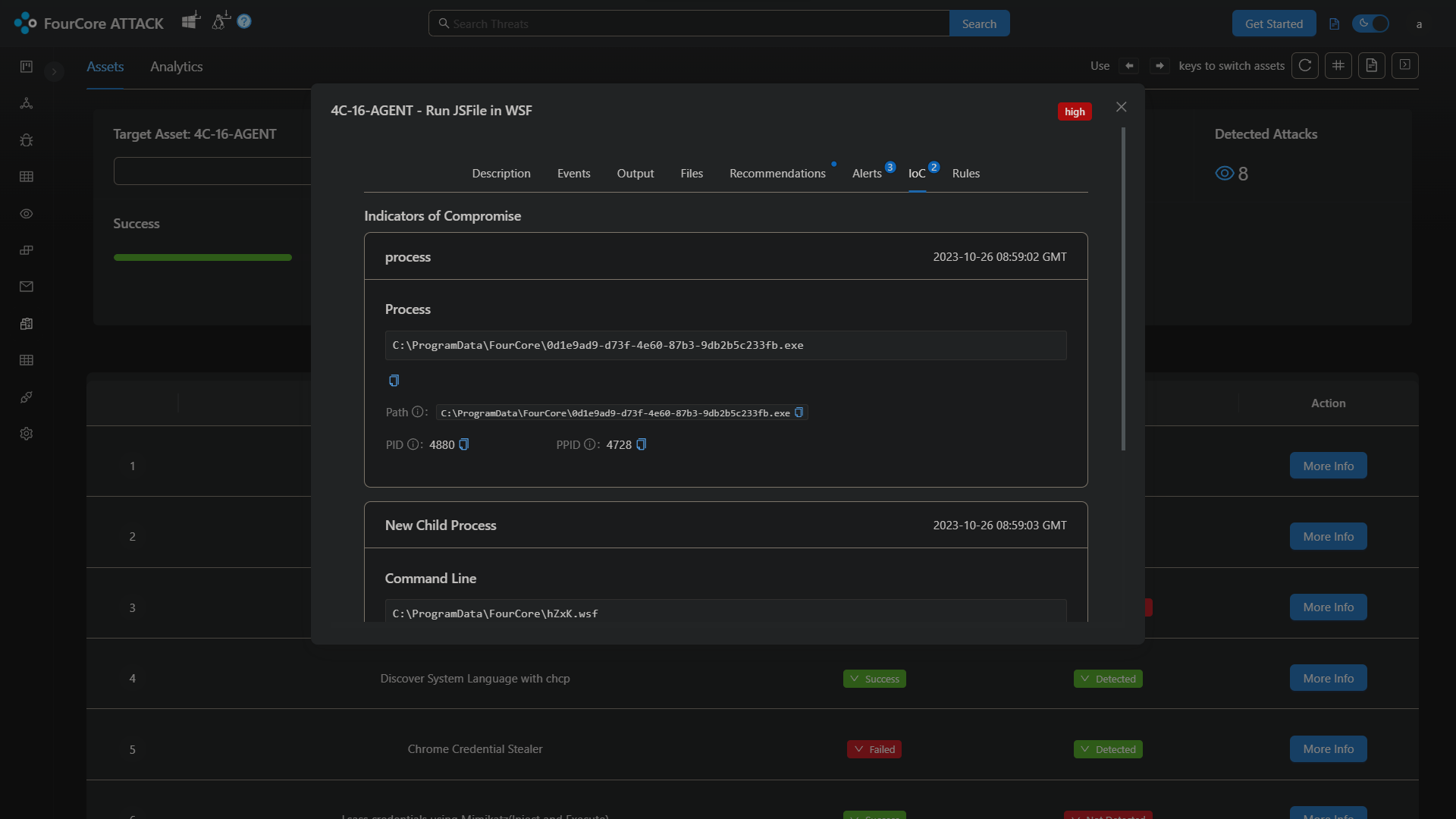
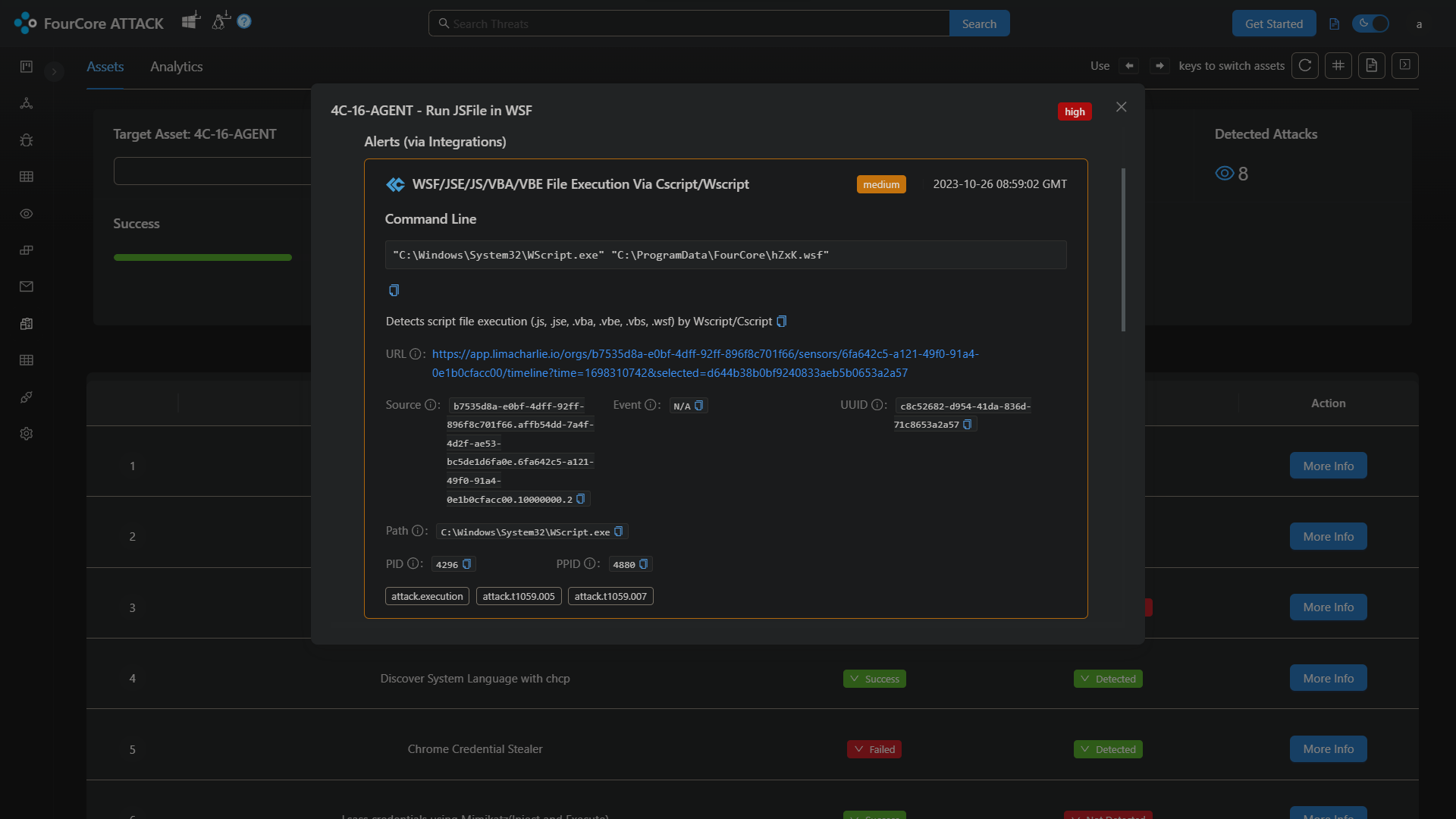
The WSF script execution was detected by the existing rulesets as a suspicious wscript execution. The implant executes this script as if it was double-clicked by a user from the desktop, this makes actual execution become a child of WmiPrvSe.exe instead of the stager executable. Thus creating a split process tree.
We can inspect the process tree and validate the execution of wscript.exe from the stager executable.
Success and Detections
Similarly, 8 out of the 17 total techniques were detected, while 12 out of the 17 techniques were successful. For the attacks that were not detected, we can build detections using the Sigma rules and IoCs associated with the attacks, using the LimaCharlie detection YAML and the telemetry collected by the LimaCharlie agent.
FourCore + LimaCharlie = Threat-informed Defense
FourCore ATTACK integrated with LimaCharlie makes validations continous and real-time, allowing red and blue teams to collaborate on understanding offensive techniques and how they can be detected. The IOCs on the FourCore ATTACK platform give for a evidence-based method to validate threats and their detections. LimaCharlie has a powerful rule language which makes it simple for detection engineers to write rules that can detect the most imminent threats.

