Threat-informed defense with HarfangLab EDR and FourCore ATTACK

Threat-Informed Defense with HarfangLab EDR and FourCore ATTACK
Attackers are constantly refining their methods, and as defenders, we must continuously upskill our defenses and teams. Adversary Emulation, a critical component of a threat-informed defense strategy, allows us to mimic real-world threats, providing tangible evidence of our detection and response capabilities. This proactive approach helps us track security coverage and identify gaps against the most relevant threats to our organization.
If you take a pentest and follow a specific threat-actor's tactics, techniques and procedures, that is emulation of the threat. There are various open-source adversary emulation tools to simulate cyber attacks. In this blog, we will use the FourCore ATTACK platform to emulate threats and HarfangLab EDR to build and validate a detection infrastructure.
Our goal is to make offensive security accessible and continuous – helping security teams, red and blue alike, of all skill levels to be armed with expert capability and collaborate proactively to protect against the most imminent threats.
Setting the Stage with FourCore ATTACK
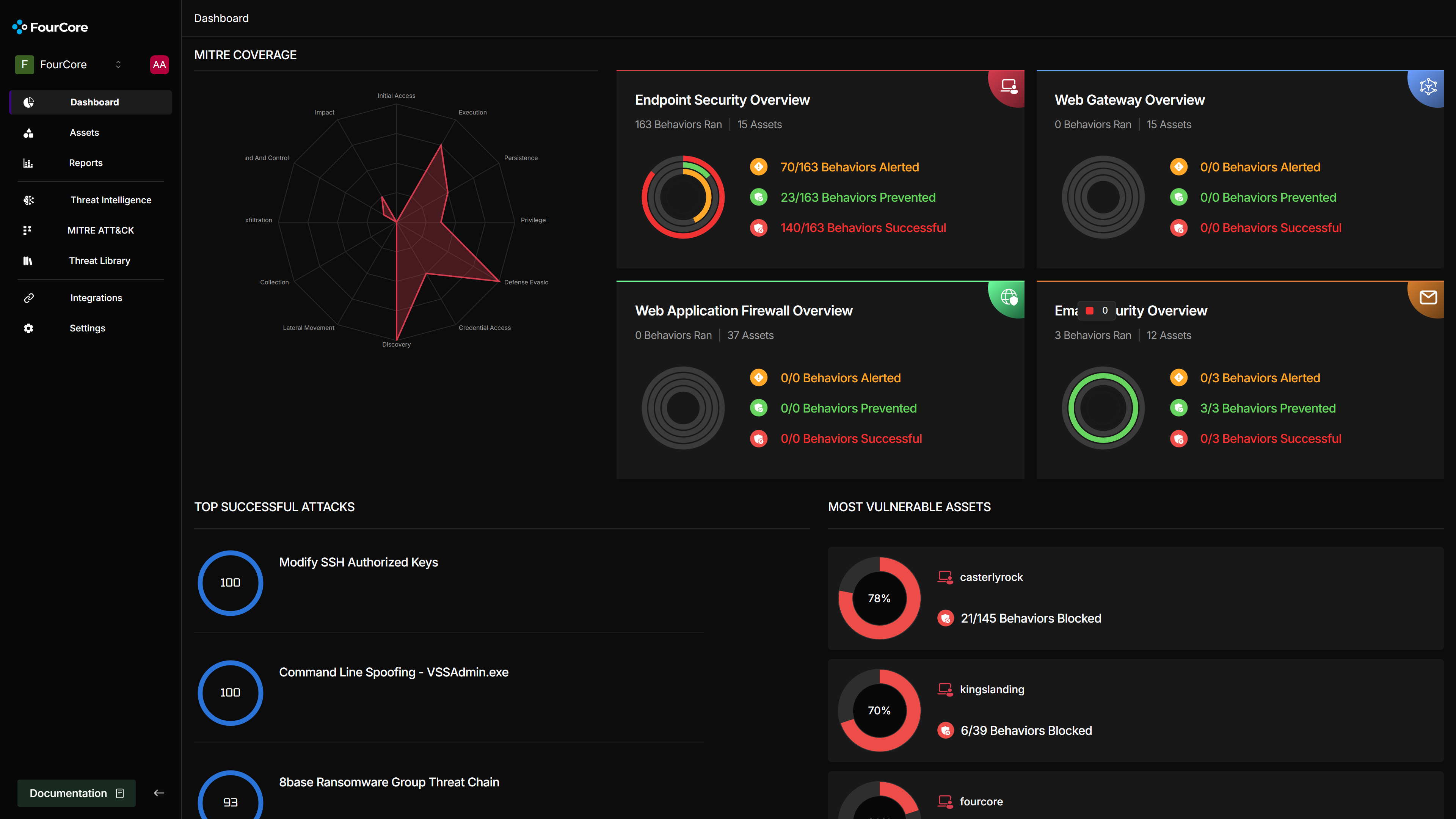
FourCore ATTACK is a SaaS platform designed for automated adversary emulation. After setting up an account, the first step is deploying an agent onto the target system. Agents are available for Windows and Linux.
For this demonstration, our target is a Windows Server 2022 machine, also equipped with the HarfangLab EDR agent. We'll use the FourCore ATTACK Agent PowerShell script for a quick deployment on our system, which we'll call "winterfell".
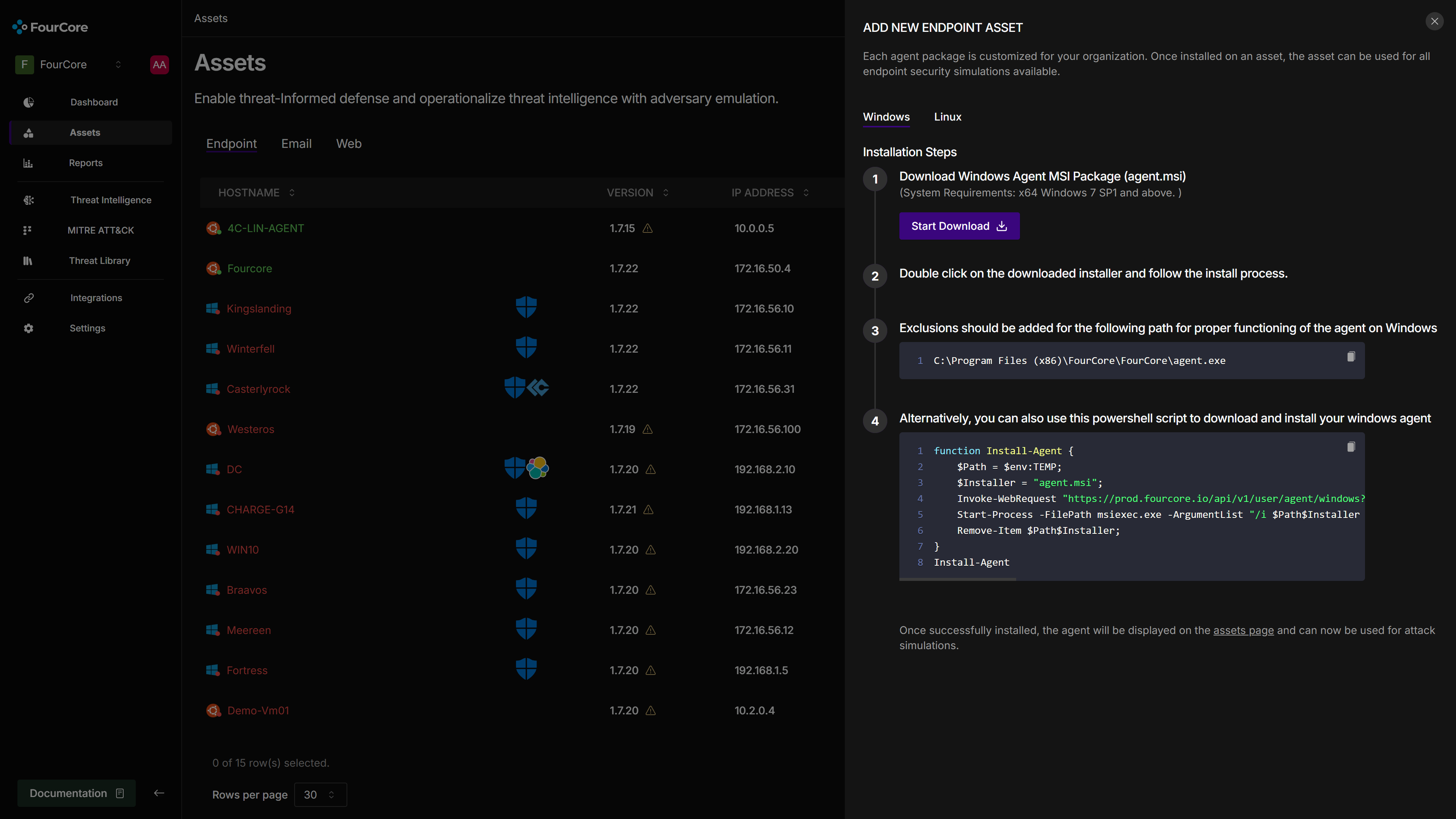
Attack Library
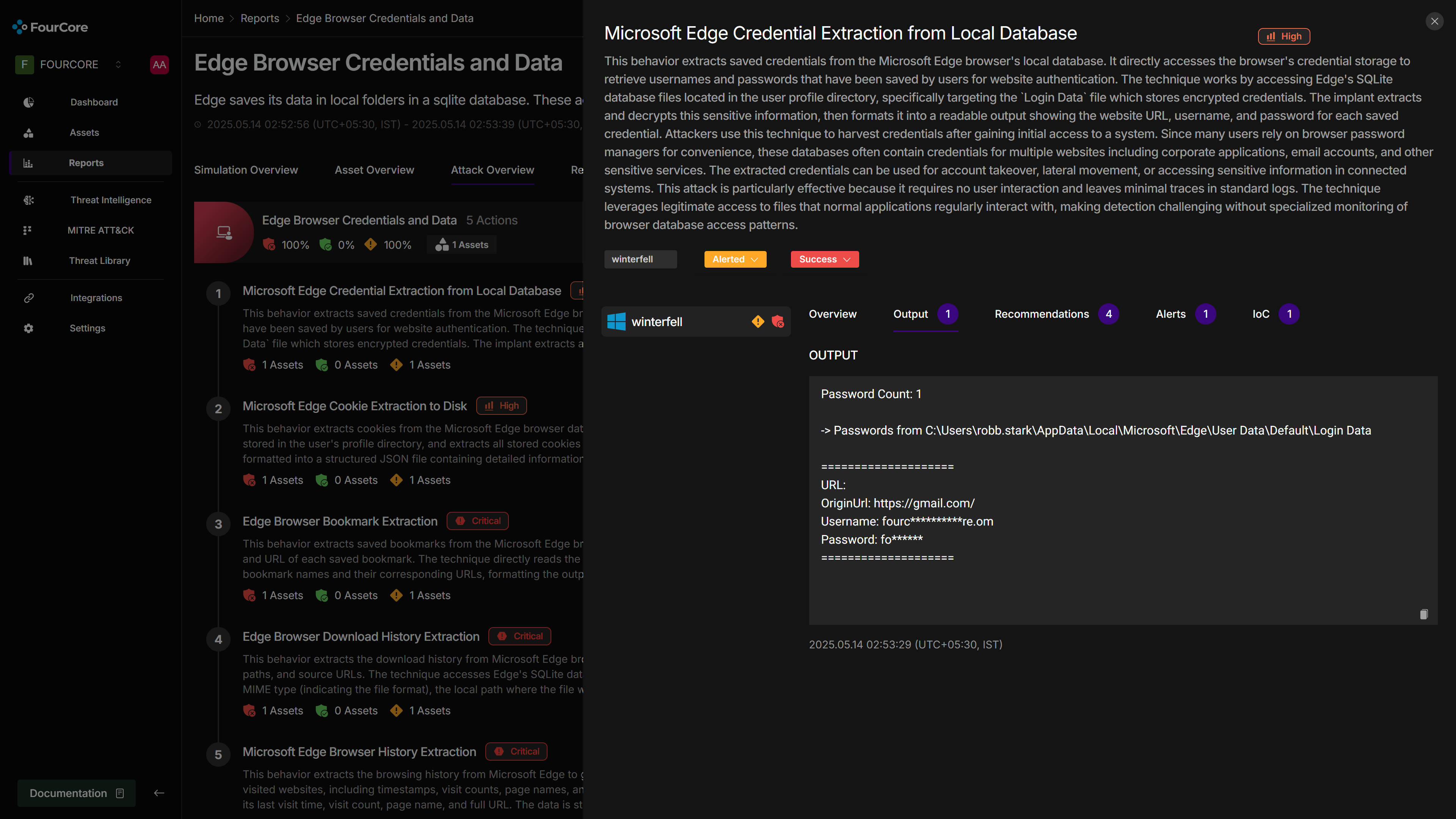
The FourCore ATTACK platform features an extensive Attack Library. All attack chains and individual actions are mapped to MITRE ATT&CK®️ techniques, allowing users to filter attacks by technique, target platform, or threat category. For this exercise, we'll select the "Edge Browser Credentials and Data" attack chain to emulate on "winterfell". We will then hunt for evidence of these TTPs and corresponding detections within HarfangLab EDR.
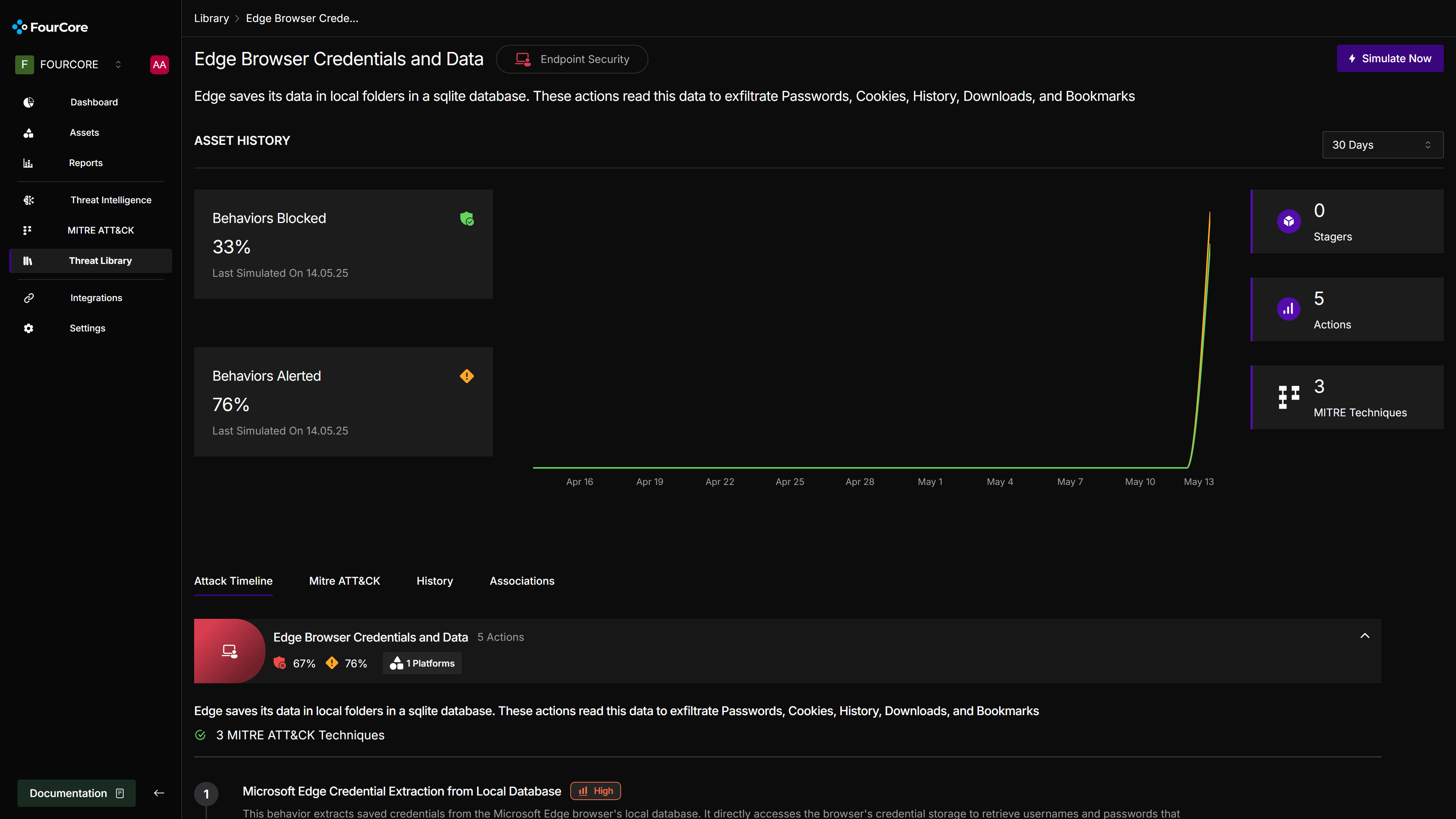
Edge Browser Credentials and Data Theft Emulation
We initiate the "Edge Browser Credentials and Data" attack chain emulation on "winterfell". This chain is designed to mimic attacker techniques for exfiltrating sensitive user data stored by the Microsoft Edge browser.
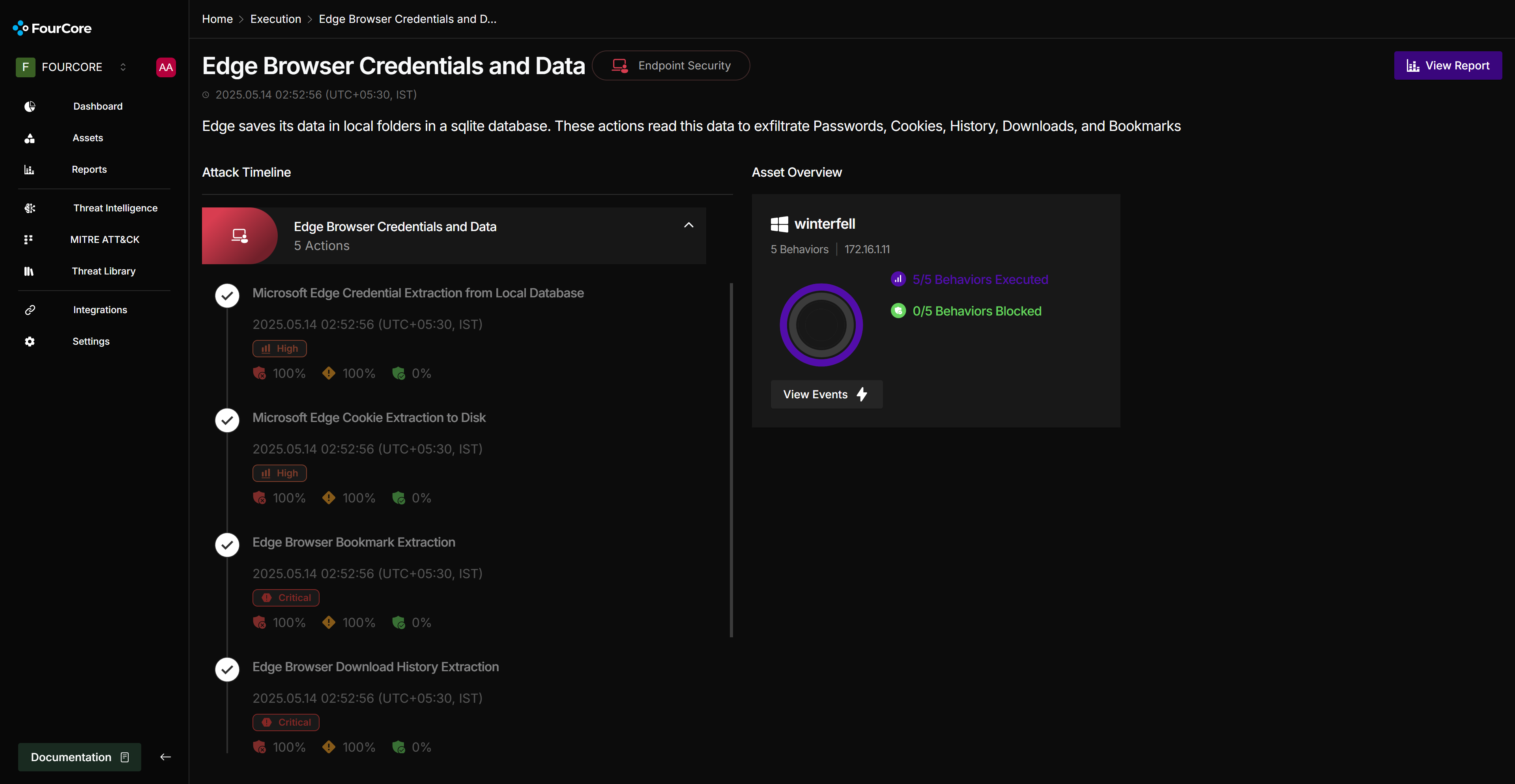
The "Edge Browser Credentials and Data" attack chain executes the following actions:
- Fetch Credentials: Extracts saved usernames and passwords from Edge's
Login DataSQLite database. - Fetch Cookies: Extracts cookies from Edge's cookie database, potentially allowing session hijacking.
- Fetch Bookmarks: Extracts user bookmarks, which can reveal sensitive internal sites or user interests.
- Fetch Downloads: Extracts the download history, potentially identifying sensitive downloaded files.
- Fetch History: Extracts browsing history for reconnaissance.
Throughout the emulation, FourCore ATTACK collects detailed information for each action, including status, logs, generated IoCs (like paths to SQLite databases accessed), command outputs (the exfiltrated data itself), and any files created (e.g., JSON output of cookies).
HarfangLab EDR – The Detection Powerhouse
HarfangLab EDR provides comprehensive endpoint detection and response through a multi-layered approach. All detection is performed at the agent level through a suite of detection engines including:
- Sigma: For behavioral analysis.
- YARA: For signature-based detection.
- IOC Engine: For matching known indicators of compromise.
- HL-AI: HarfangLab's proprietary AI engine for detecting anomalous behavior.
- Ransomguard: Dedicated anti-ransomware engine.
- Sidewatch: Heuristic DLL sideloading detection.
- Kernel Callback Tampering Prevention: Protects the EDR's own telemetry sources.
Endpoint behavior and detection capabilities are managed through granular policies, allowing administrators to tailor protection to different groups of assets.
Bridging Offense and Defense: Integrating FourCore ATTACK with HarfangLab EDR
The synergy between FourCore ATTACK and HarfangLab EDR allows for a robust threat-informed defense cycle. FourCore ATTACK emulates adversarial TTPs, and HarfangLab EDR is monitored for corresponding detections.
Integration is achieved via HarfangLab's API. An API token can be generated from the HarfangLab Manager under Administration > Users > [User] > Configure User > Generate API Token.
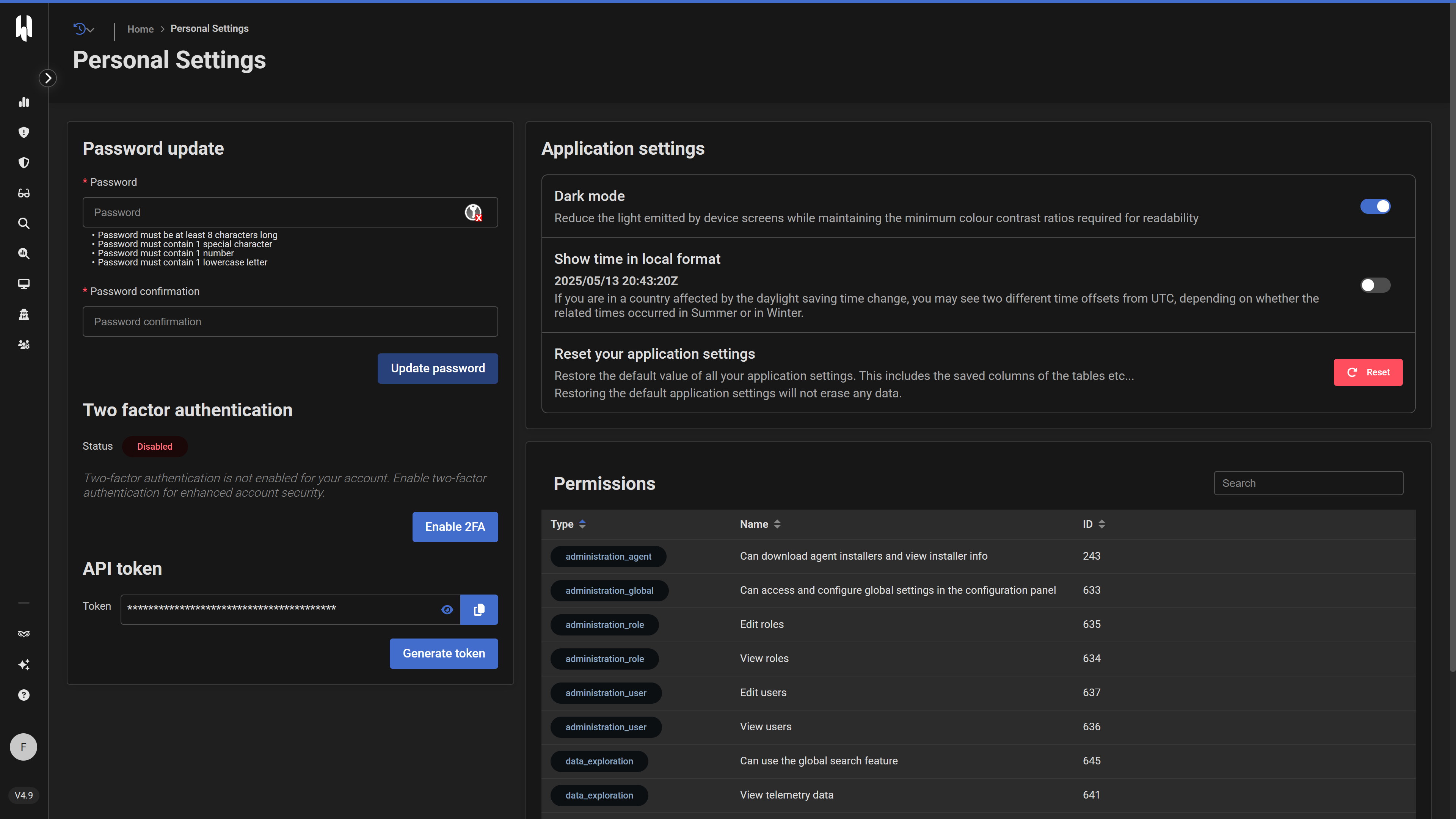
This API token is then configured within the FourCore ATTACK platform's integration settings for HarfangLab EDR. Once configured, FourCore ATTACK can query HarfangLab EDR to automatically correlate emulated attack actions with generated security events and alerts, using IoCs reported by the emulated attacks.
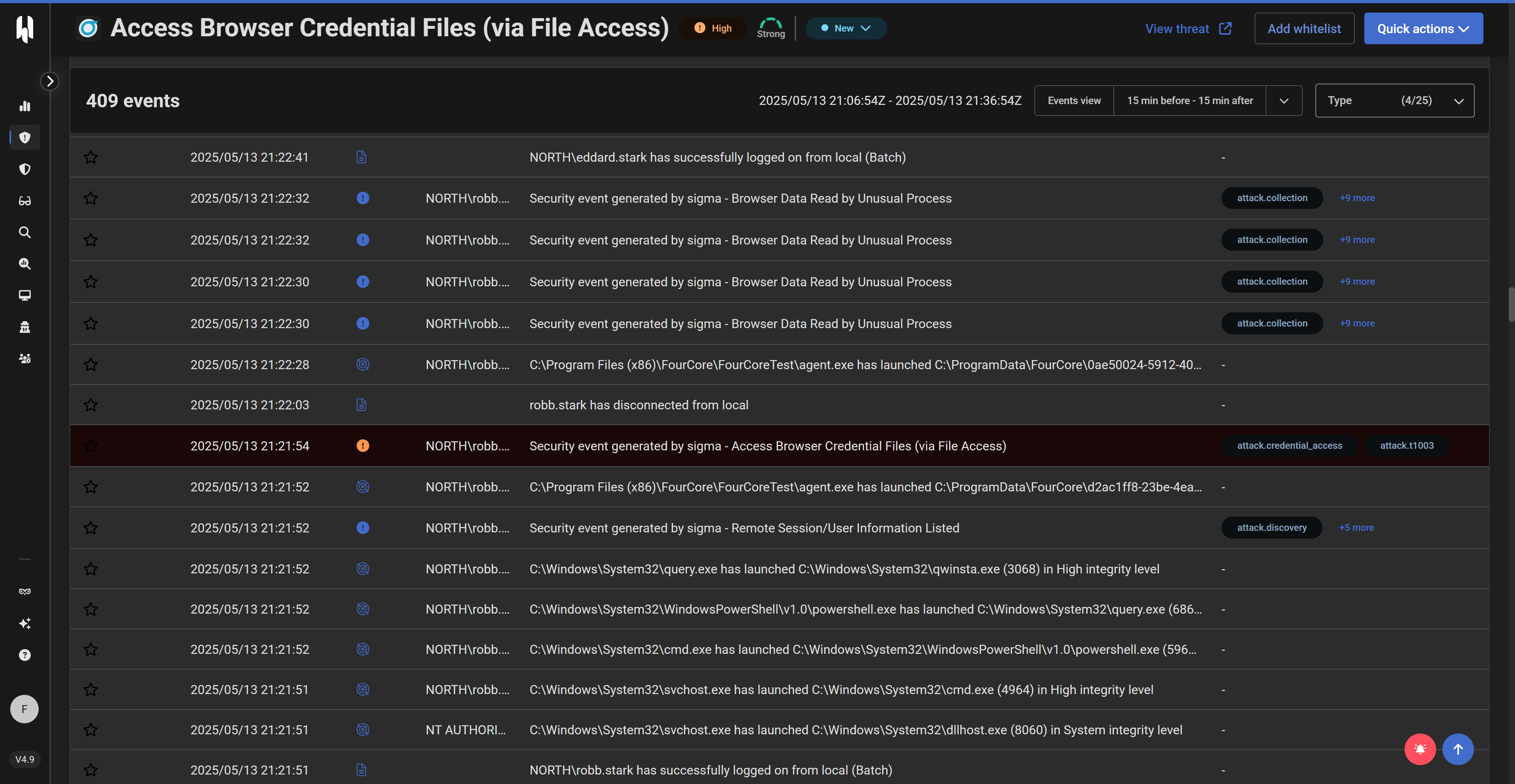
Uncovering Edge Browser Data Theft in HarfangLab EDR
After running the "Edge Browser Credentials and Data" emulation with FourCore ATTACK, we turn to the HarfangLab EDR console to observe the detections. HarfangLab's diverse detection engines are well-equipped to identify various TTPs employed by Qakbot. We would typically navigate to the Detection > Threats or Detection > Security Events views.
Let's examine potential detections for these actions:
Microsoft Edge Credential/Cookie/History Extraction
These actions involve the FourCore ATTACK implant directly accessing SQLite database files within the Edge user profile directory (e.g., Login Data, Cookies, History). HarfangLab EDR could detect this through:
- Sigma Engine:
- Rules monitoring for
file_readorfile_accessevents targeting sensitive browser database files (e.g.,*\Microsoft\Edge\User Data\Default\Login Data,*\Microsoft\Edge\User Data\Default\Cookies,*\Microsoft\Edge\User Data\Default\History). - Rules looking for non-browser processes (like the FourCore agent or a spawned utility) accessing these files.
- The
Filesystem Eventscategory in Sigma is key here.
- Rules monitoring for
- HL-AI Engine: If the access pattern by the FourCore agent to these specific, sensitive files is deemed anomalous compared to typical system behavior.
- IOC Engine: If the FourCore agent executable itself (or its hash) were added as an IOC, though this is less about the behavior and more about the tool.
Within HarfangLab, we would scrutinize security events related to file access. The Timeline view for "winterfell" would be crucial to see the sequence: FourCore agent process -> file read operation on Login Data. The Data Explorer for the agent, specifically under Telemetry > Filesystem Events, would also contain this information.
If the attack involves decrypting credentials (Edge uses OS-level DPAPI), any suspicious API calls related to decryption (if monitored by HarfangLab's telemetry) could also trigger Sigma rules.
Validating and Enhancing Detections
The FourCore ATTACK platform provides a report detailing which TTPs were successfully executed and which were blocked or failed. This report, along with its IoCs (e.g., paths to accessed SQLite files, hashes of any temporary files created), is then compared against the alerts and telemetry in HarfangLab EDR. The integration automatically correlates these, showing which HarfangLab alerts correspond to specific emulated actions.
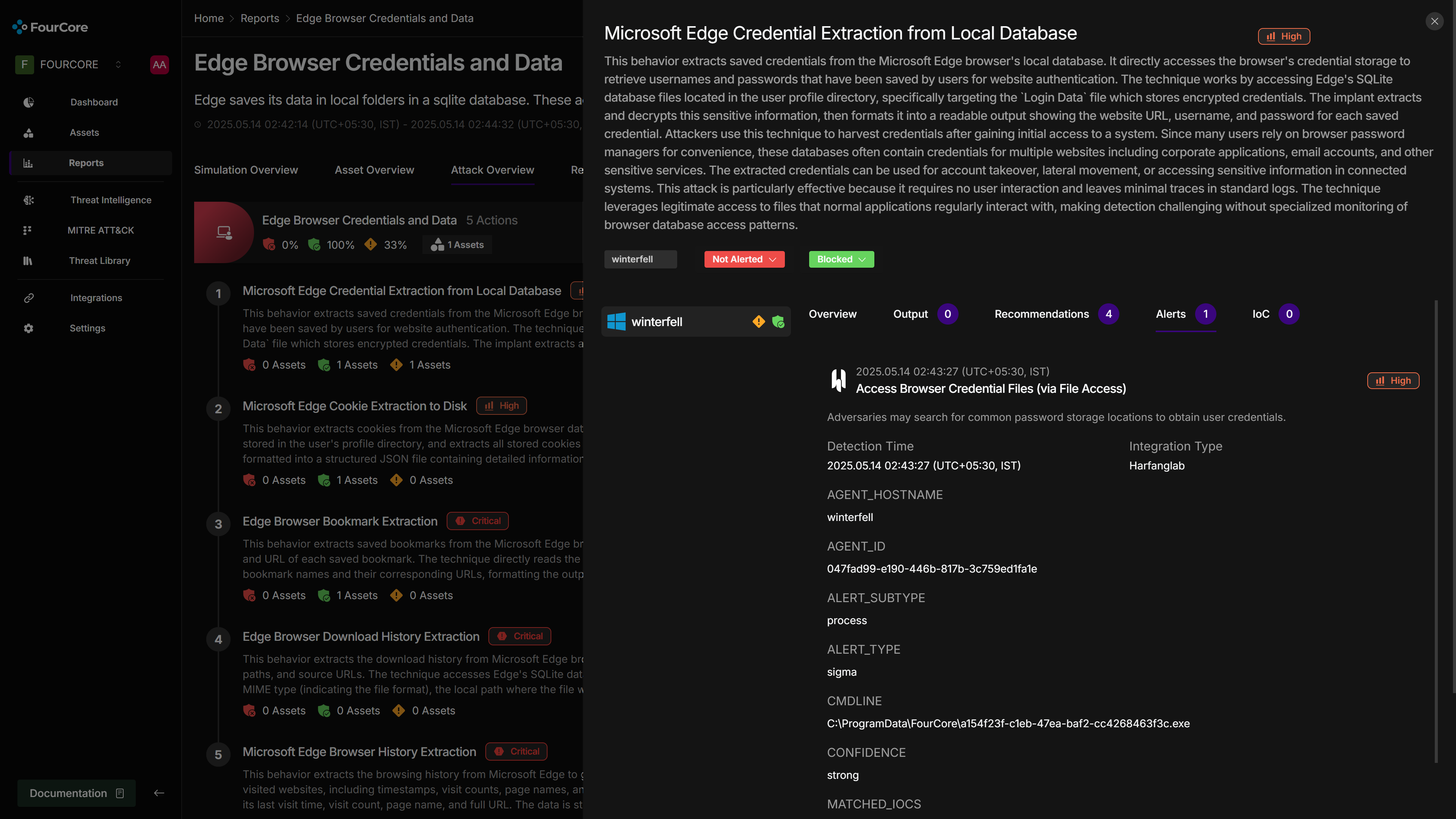
If an action like "Microsoft Edge Credential Extraction from Local Database" was successful in FourCore ATTACK but did not generate a high-fidelity alert in HarfangLab EDR, this signifies a detection gap. To address this:
- Analyze the logs and IoCs from FourCore ATTACK for the missed action. Note the exact file paths accessed (e.g.,
%LOCALAPPDATA%\Microsoft\Edge\User Data\Default\Login Data). - Leverage HarfangLab's Threat Intelligence section to create new detection rules.
Implementing a Sigma Rule for Browser Credential File Access
To enhance detection for this specific TTP, we can implement the following Sigma rule in HarfangLab EDR:
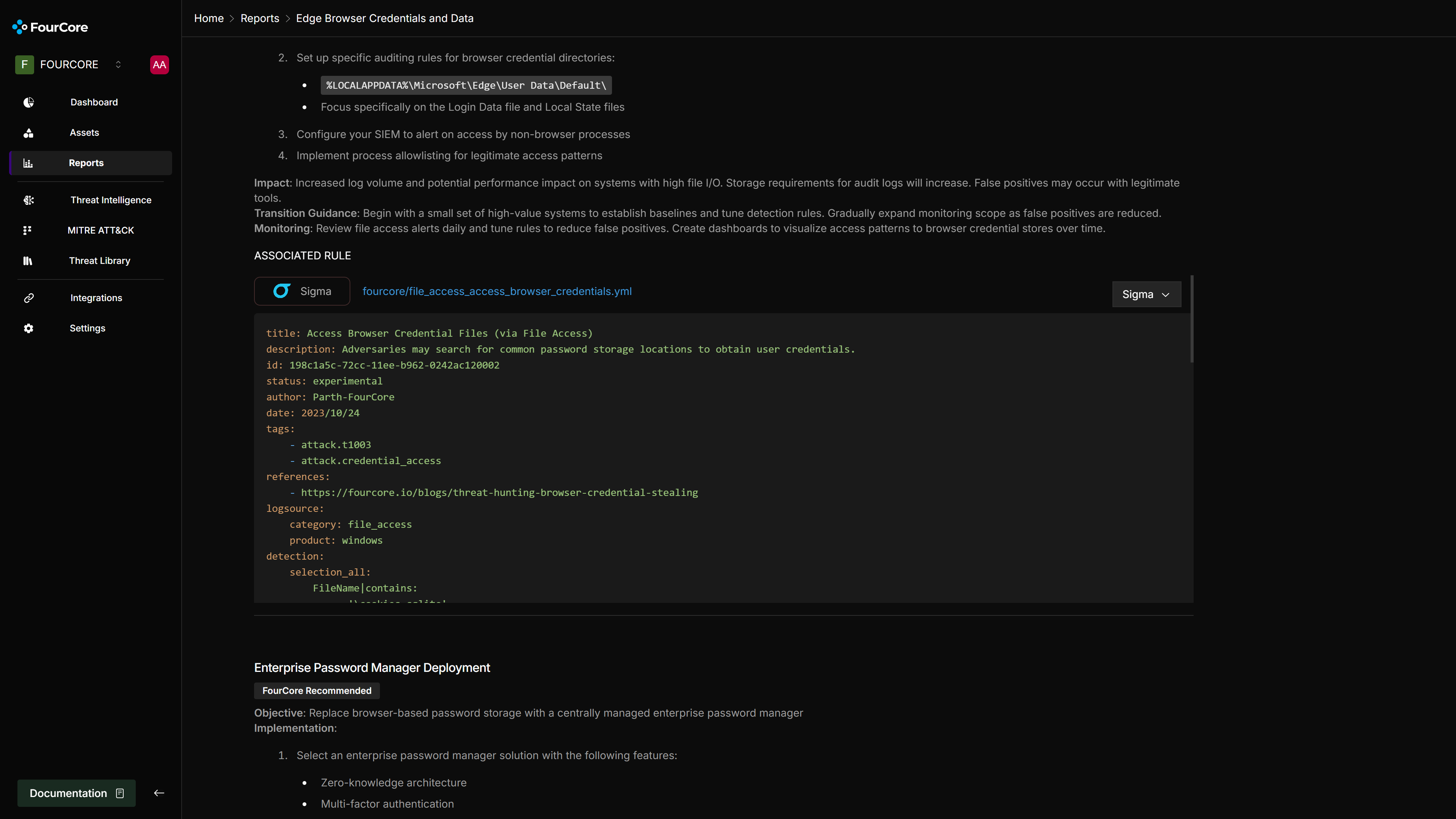
Steps to add this Sigma rule to HarfangLab EDR:
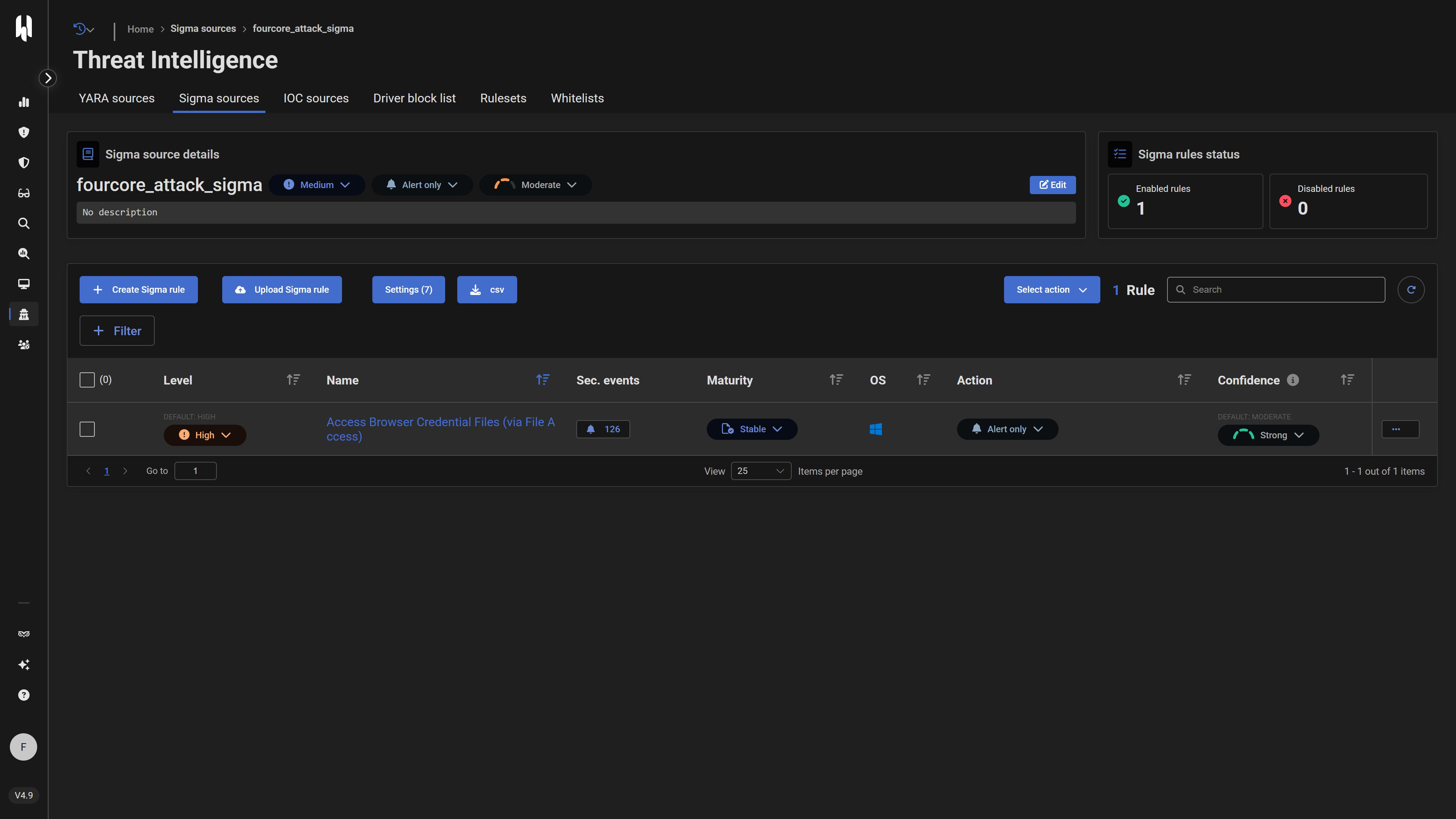
- Navigate to Threat Intelligence > Sigma.
- Select an existing custom source or Create source (e.g., "Custom Browser Detections").
- Within the source, click Create rule or Upload Sigma file.
- If creating manually, paste the YAML content into the editor.
- Set the Maturity to "Experimental" initially.
- Configure the Allowed actions (e.g., "Alert only" for testing).
- Save the rule.
- Re-run the "Edge Browser Credentials and Data" attack chain in FourCore ATTACK to validate that the new Sigma rule in HarfangLab now triggers an alert.
- Observe the generated security events. If legitimate processes are flagged, refine the
filter_*sections in your Sigma rule or create specific Whitelists in HarfangLab EDR (e.g., whitelisting a legitimate backup tool'sImagewhen it accessesPathcontainingLogin Data).
This iterative process of emulate-detect-enhance strengthens the overall security posture against common credential and data theft techniques.
FourCore ATTACK + HarfangLab EDR = A Robust Threat-Informed Defense
Integrating FourCore ATTACK with HarfangLab EDR provides a powerful framework for continuous security validation. It allows security teams to:
- Proactively identify detection gaps against real-world TTPs, such as browser data theft.
- Validate the effectiveness of existing HarfangLab detection engines and custom rules.
- Prioritize security efforts based on observed weaknesses.
- Enhance collaboration between offensive (red team/emulation) and defensive (blue team/SOC) functions.
- Build an evidence-based understanding of their security posture against specific threats.
By combining automated adversary emulation with a comprehensive EDR solution like HarfangLab, organizations can significantly improve their resilience against sophisticated cyber-attacks and truly embrace a threat-informed defense.

