Last Updated on Wed Jan 04, 2023
Honey, I shrunk the SOC: Measuring Threat Visibility with MITRE ATT&CK(R)

The SOC is at the core of protecting the organization. And the teams toil the hours to ensure they spend more time detecting threats and not just reading logs. Understanding where the SOC stands in its capability to prevent threats might almost seem an art.
Thankfully, the shift towards threat-informed Defense is helping it become a science. We can now understand, measure and regularly monitor the complexities of known and unknown Threats with MITRE ATT&CK.
We are excited to partner with Tidal Cyber and join the Tidal Product Registry to help pave the way forward for threat-Informed defense. The Tidal Product Registry now contains the repository of attack simulations available on the FourCore ATTACK platform.
You can sign up for the Tidal Cyber Community Edition registration from here.
Signal To Noise
This is a tweet from @SiliconShecky. It highlights the struggle security analysts and security teams face. Even with the best security solutions in place and teams of many individuals, It can be challenging to focus on which alerts and threats are most relevant.
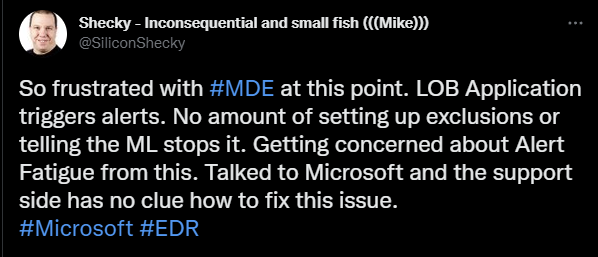
Millions of logs stream into the SIEM from various sources and hundreds of assets. This generates a large number of alerts which hide the real threats which need immediate response between these alerts.
Alert Fatigue happens when the overwhelming number of alerts generated from these logs desensitize and burn out analysts having to sift through them. Responding to incidents and containing them becomes challenging and highly reactive before it has done damage.
A great security leader taught me that you could never get foolproof security, but to be secure means having the minimum blast radius and the least impact on the organization.
At FourCore, we want to empower the SOC to proactively build better visibility of relevant threats before they are compromised, making life easier for those handling incidents day in and out with threat-informed defense.
Empowering the SOC with threat-informed defense
Threat-informed defense is a strategy to proactively strengthen defenses against the tactics attackers employ before they actually do. Focused on building a deep understanding of adversary tactics, techniques and procedures. At the highest level, it can help you build a scientific and measurable understanding of where your detection and response capability stands today and how to move it upwards.
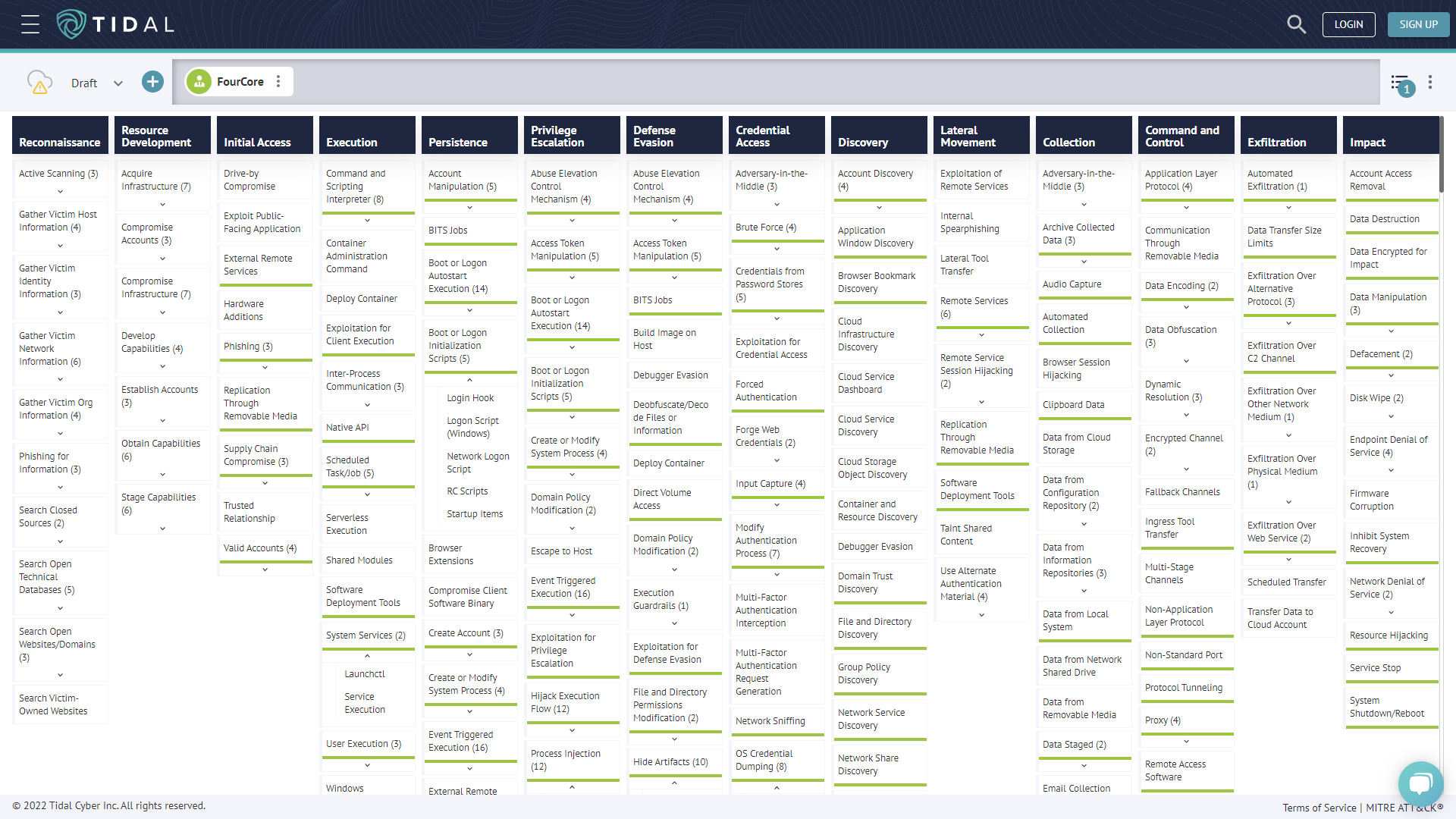
MITRE ATT&CK(R) is at the core of threat-informed defense. It is a powerful framework used by defenders across the globe to share information on threat actor behaviour. However, there are still challenges with operationalizing MITRE ATT&CK.
- Can we detect techniques in the ATT&CK matrix?
- How can I identify threats relevant to my industry and organization?
- How to measure my SOCs coverage for detecting techniques in the ATT&CK matrix?
The Tidal Cyber platform can be leveraged to operationalize the ATT&CK Matrix effectively. The Tidal Cyber platform provides a flexible ATT&CK matrix, threat intelligence mapped to the ATT&CK matrix, and the Product Registry to identify if your security solutions offer detections for those threats and how to validate them with adversary emulations.
Assess, Validate And Remediate
We’re excited to partner with Tidal and release our repository of simulations on the Tidal platform, which can map vendors' detections to adversary emulationss on the FourCore ATTACK platform.
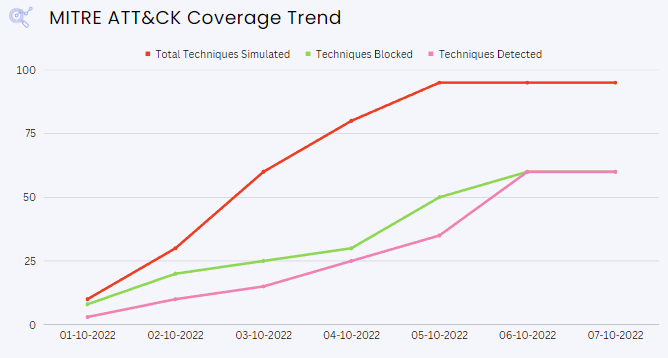
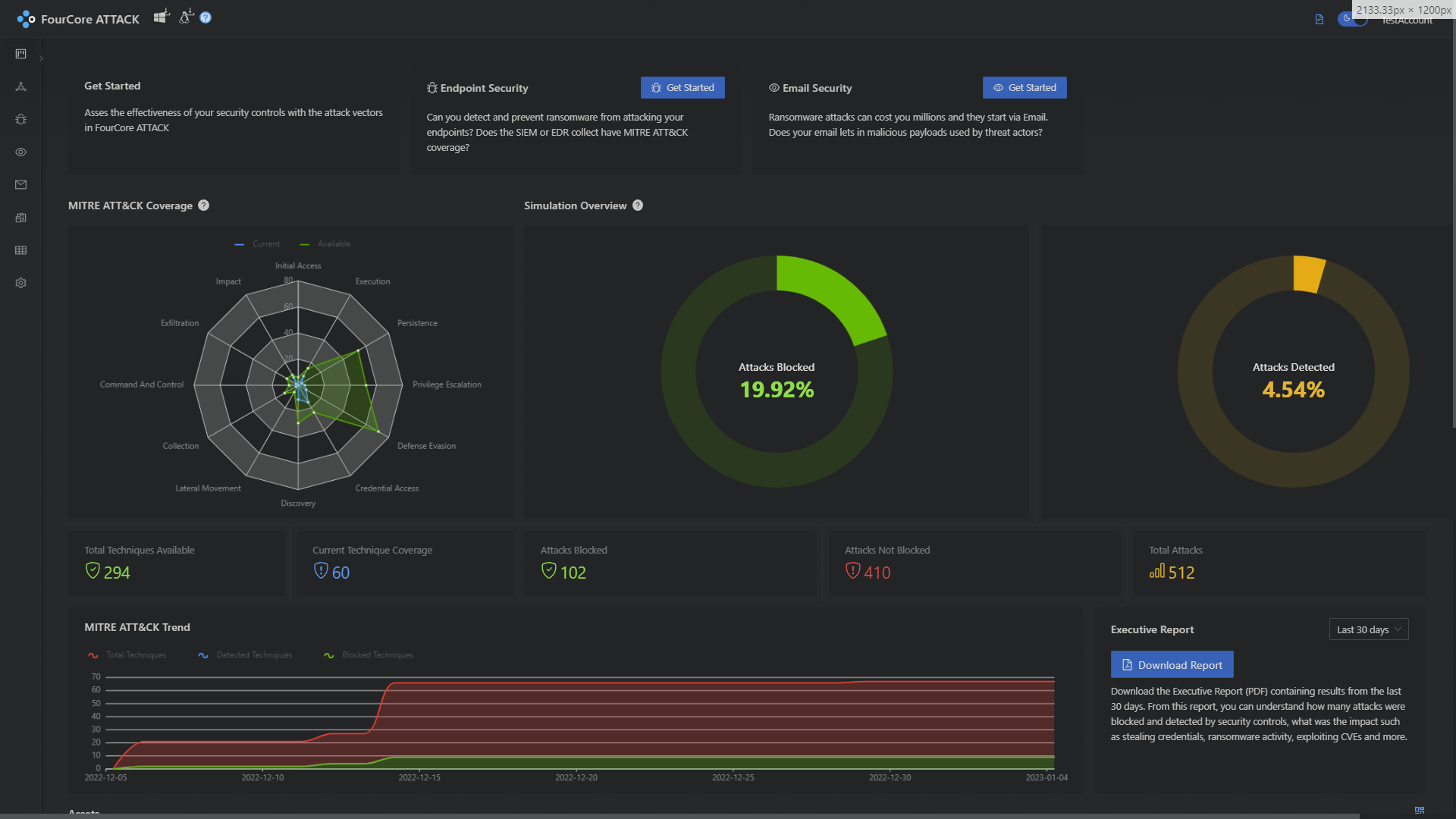
Understanding coverage of ATT&CK may seem vague. Tidal and FourCore are working together to make it a measurable and automated process. Tidal’s platform brings context to the adversary emulations capabilities in the FourCore ATTACK platform.
You can assess your detection capability, validate them with adversary emulations and remediate them by extending your existing security tools with open rules such as Sigma and Yara.
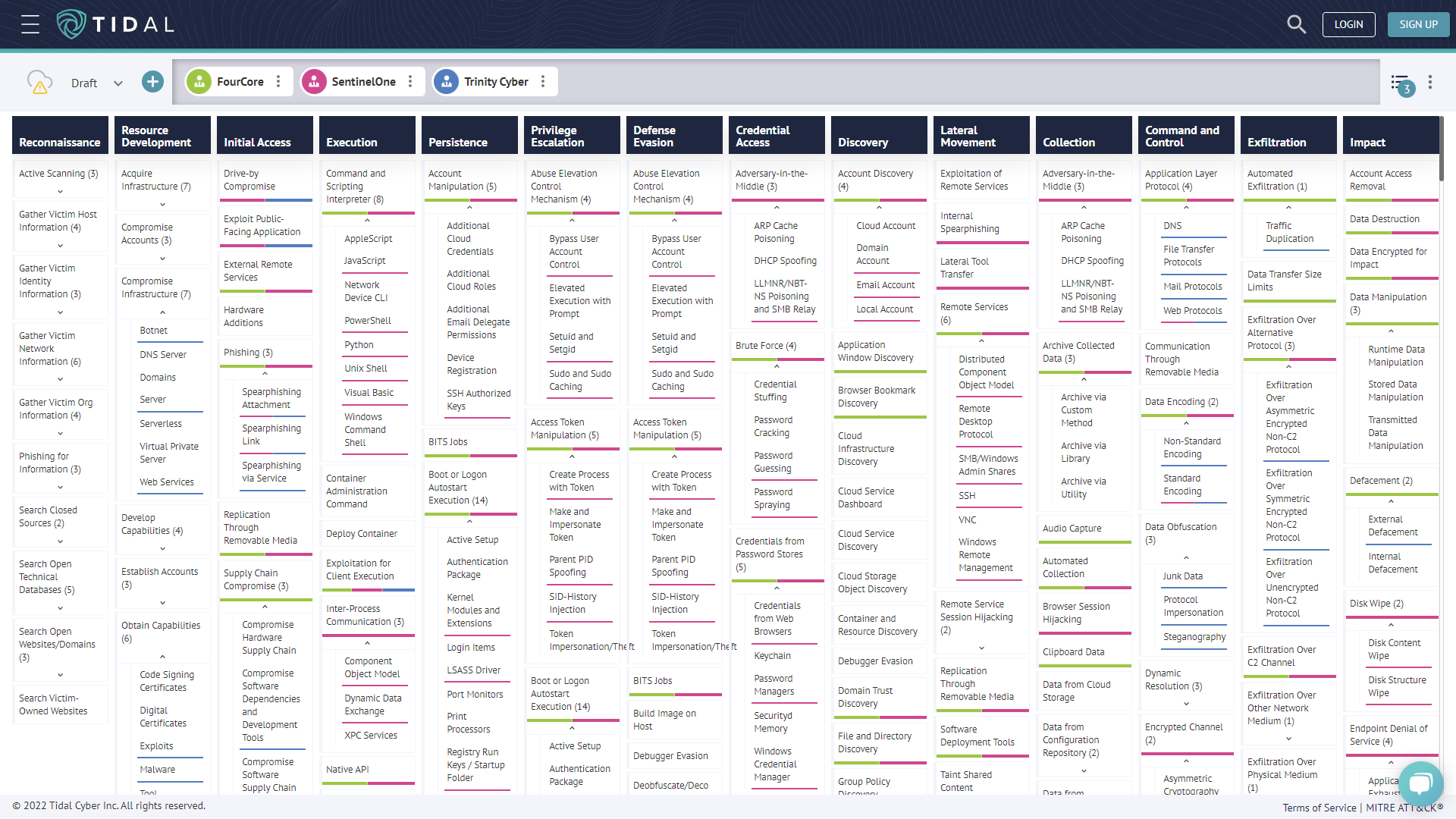
The above image shows the adversary emulationss offered in the FourCore ATTACK platform combined with the detection capabilities of different security solutions.