firedrill: an open source malware simulation harness

TL;DR: firedrill is an open-source library from FourCore Labs to build malware simulations quickly. We have built a set of four different attack simulations for you to use and build on top of Ransomware Simulation, Discovery Simulation, UAC Bypass, and Persistence Simulation. Download them now from the firedrill GitHub repo. In addition, you can use the firedrill binaries to find out how effective your antivirus is or if your sandbox is detecting the proper signatures.
The Enterprise MITRE ATT&CK matrix has over 150 techniques and 379 sub-techniques. It is a curated information base and standard for cyber adversary behaviour, exhibiting the different aspects of an adversary's attack lifecycle and the platforms they are identified to target. Thus, becoming a popular template for building detection and response programs. Building on these techniques and sub-techniques, we can quickly test our security solutions' effectiveness against a wide variety of real-world attacks.
However, how exactly should one perform these tests? They can organize a red team engagement, and red-teamers use their expertise and bespoke tools to evaluate their infrastructure. One can use open-source solutions such as Atomic Red Team and MITRE CALDERA. MITRE even does a evaluation of cyber security products against behaviours of APT groups mapped against the ATT&CK matrix.
We have built a malware simulation harness called firedrill to build native attack simulations in Go. At FourCore Labs, we work on a breach and attack simulation platform: FourCore ATTACK. Our goal is to help enterprises improve their security posture and validate the effectiveness of their security controls. firedrill is a derivative of our work on FourCore ATTACK, and we are releasing a few of the native attack simulations available in ATTACK as part of firedrill. With firedrill, we have built a simple yet powerful malware simulation harness to build cross-platform attack simulations in Go.
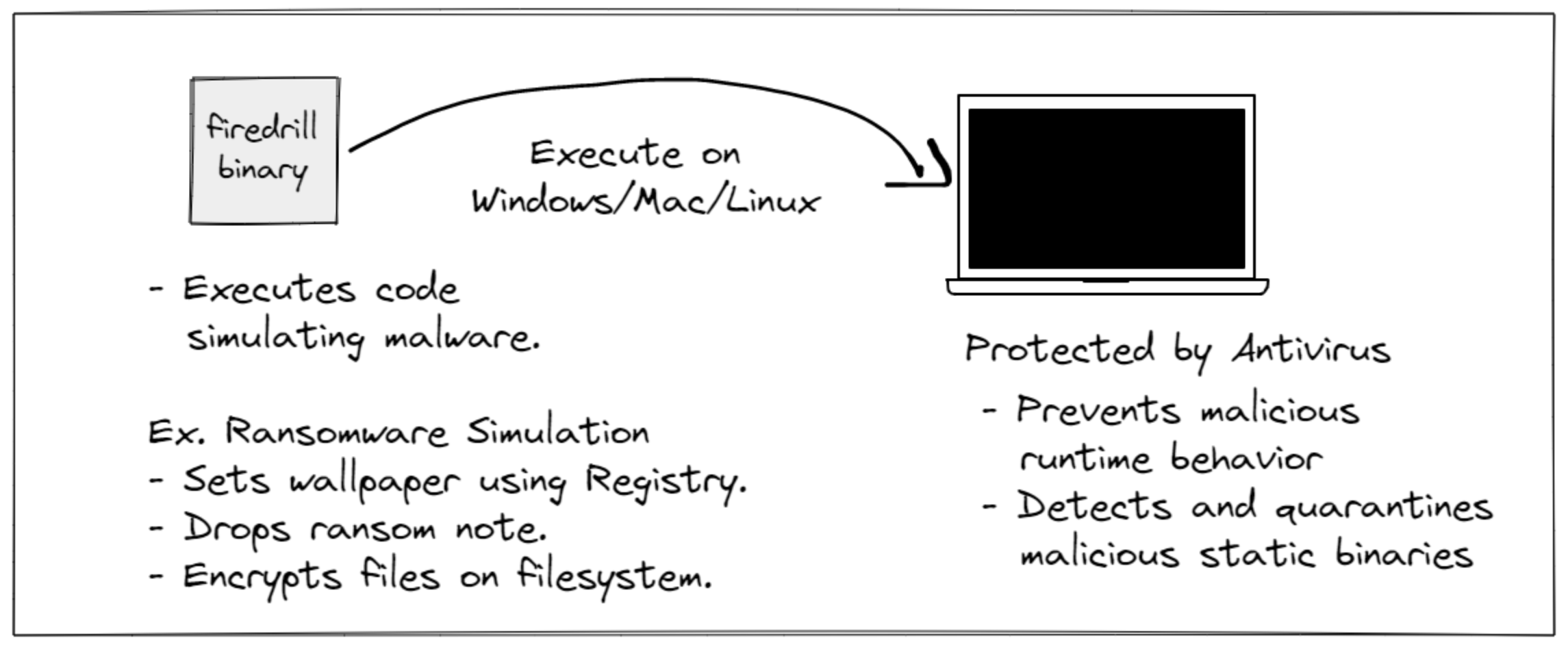
Each binary produced through the firedrill platform performs specific behaviour mapped to various tactics and techniques in the MITRE ATT&CK matrix and possible behaviours detected by endpoint protection solutions.
At the time of writing, one can find four different simulations in the GitHub releases built for windows/amd64: Discovery, Run Key Registry persistence, fodhelper.exe UAC Bypass and a ransomware simulation. Using these simulations is straightforward: download the release and execute the binaries on their system. They can try different methods of executing the binaries for different run-time signatures, using a stager, or be creative by providing admin privileges. If one intends to use the binaries from the Github Releases, all the binaries are obfuscated to prevent static signature detection on the binary.
We have taken care of one important thing: each simulation is a non-intrusive safe simulation and does not perform any destructive action on the system.
Ransomware Simulation
The ransomware simulation binary aims to perform the typical behaviour of ransomware.
This simulation includes, in this order:
- Encryption of files on the filesystem (only test files dropped by the binary and )
- Dropping a ransom note on the desktop
- Changing the system wallpaper through registry keys (and restoring it after some time)
The video is how the simulation runs and performs malicious behaviour. The logs will help one understand the exact steps taken by the simulation. They can also put this binary in a sandbox that can detect these common ransomware signatures. Check out the ransomware analysis on Hybrid-Analysis.

Discovery Simulation
The discovery simulation consists of a simulation of a malware executing three techniques from the Discovery tactic in MITRE ATT&CK, performing reconnaissance of system information which is used for further exploiting the system:
This simulation includes, in this order:
- Discovering the running processes on the system
- Discovering the peripherals present on the system
- Discovering the software installed on the system with their respective versions
The video is how the simulation runs and performs discovery behaviour. The logs will help one understand the exact steps taken by the simulation. They can also put this binary in a sandbox to detect these common signatures of a discovery payload. Check out the analysis of the discovery simulation on Hybrid-Analysis.
UAC Bypass Simulation
The UAC Bypass simulation consists of malware using the fodhelper.exe utility available from Windows 10 to achieve local privilege escalation by creating a registry structure to execute arbitrary commands with administrator privileges:
This simulation includes, in this order:
- Create a new registry structure in
HKCU:\Software\Classes\ms-settings\and startnotepad.exewith admin privileges bypassing UAC
The video is how the simulation runs and performs Local Privilege Escalation(LPE)/UAC Bypass behaviour. The logs will help one understand the exact steps taken by the simulation. They can also put this binary in a sandbox to detect these common signatures of a UAC Bypass or LPE payload. Check out the analysis of the LPE simulation on Hybrid-Analysis.
Registry Run Key Persistence Simulation
This is a simulation of persistence techniques that use Registry Run keys to achieve persistence for arbitrary payloads. These keys include: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run, EY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce, HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServices, HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce.
This simulation includes, in this order:
- Add a value in the registry key at
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Runto execute a sample payload embedded in the binary. - Delete the value from
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Runto bring back it to it's original state for a safe simulation.
The video is how the simulation runs and performs Persistence behaviour. The logs will help one understand the exact steps taken by the simulation. They can also put this binary in a sandbox to detect these common signatures of a Persistence payload. Check out the analysis of the registry run key simulation on Hybrid-Analysis.
Build your own behaviours
If one is comfortable with Go, it is simple to create new behaviours for their use case. New behaviours require implementing the sergeant.Runnable interface.
1type Runnable interface { 2 ID() string 3 Name() string 4 Run(ctx context.Context, l *zap.Logger) error 5}
The Run function passes a context and logger. Build on top of the Run function to implement their behaviours.
Building a new binary requires creating a new main package under cmd/ and initializing an instance of sergeant via sergeant.NewSeargent. Please refer to the existing binaries, and one can reuse the main packages for new behaviours.
We would love to see new behaviours and the analysis of existing behaviours by the community. So please an open issue if one wants to see a new behaviour or fork and create a pull request if they build one!
FourCore ATTACK
FourCore ATTACK builds on the fundamentals showcased here with firedrill. It is a breach and attack simulation platform that extends the abilities of firedrill with an extensive suite of attack simulations, mass automation of simulations across your infrastructure and regular updates of new simulations. Try FourCore ATTACK now to get an accurate security validation of your organization.