Meet FourCore @BlackHat MEA 2023

FourCore is thrilled to invite you to BlackHat 2023 Middle East and Africa. We are gearing up for our striking debut at the spectacular Black Hat MEA 2023 conference. A global cybersecurity conference and exhibition at Riyadh KSA welcoming over 40,000 infosec professionals and 300+ world-renowned speakers from over 120 countries. As a leading cybersecurity company, we aim to secure Saudi Arabia's visionary goals through our modern and proactive outlook towards cyber defenses.
Join us to discover how we make offensive security accessible for all security teams - red and blue alike and arm them with the expert capability to protect against the most imminent threats.
Event Details
-
📅 Date: 14-16 November 2023
-
📍 Location: Riyadh Front Exhibition and Convention Center, Riyadh, Saudi Arabia
-
⚓ Stand H2.G14
At FourCore, our vision is that "Real Threats lead to Real Response", and that's we can achieve Threat-informed Defense. There are three key components to Threat-informed defense: threat intelligence, purple teaming and adversary emulation.
Cyberattacks are growing daily, posing imminent threats to organisations of all shapes and sizes. To be battle-ready against adversaries, we must adopt a discipline centred around operationalising cyber threat intelligence, modelling TTPs of threat actors, emulating these tactics, techniques, and procedures (TTPs), and building collaboration between the offensive and defensive teams.
Threat-informed Defense Mini-Workshops
We are organizing three mini-workshops on Threat-informed Defense at our stall FourCore [[H2.G14]] every day from 14th - 16th November. Come to our stall at 13:30 hrs, 15:30 hrs and 17:30 hrs to learn the fundamentals of Threat-informed Defense with the FourCore team.
[[13:30]] Detection Engineering with Adversary Emulation
Unlock the true potential of Adversary Emulation to turbocharge your detection engineering efforts. Explore its profound impact on your SOC, fortifying your defenses against both familiar and novel threats.
[[15:30]] Emulating the Lockbit Ransomware
Dive into the evolution of Lockbit Ransomware and understand what made this group so notorious. Learn how to evolve your detections quicker and stop playing cat with these adversaries.
[[17:30]] Zero-Days Should Be Scared of You
Don't let zero-days haunt your cybersecurity teams! Understand why zero days are not the end of your defences. Shift the odds in your favor by focusing on post-exploitation TTPs and outsmarting the threats.
Threat-informed Defense
We must shift from a compliance/vulnerability-focused mindset to a threat-centric proactive mindset by adopting a "Threat-informed Defense" (TiD) approach.
An approach coined by MITRE, "threat-informed defense applies a deep understanding of adversary tradecraft and technology to protect against, detect, and mitigate cyber-attacks."
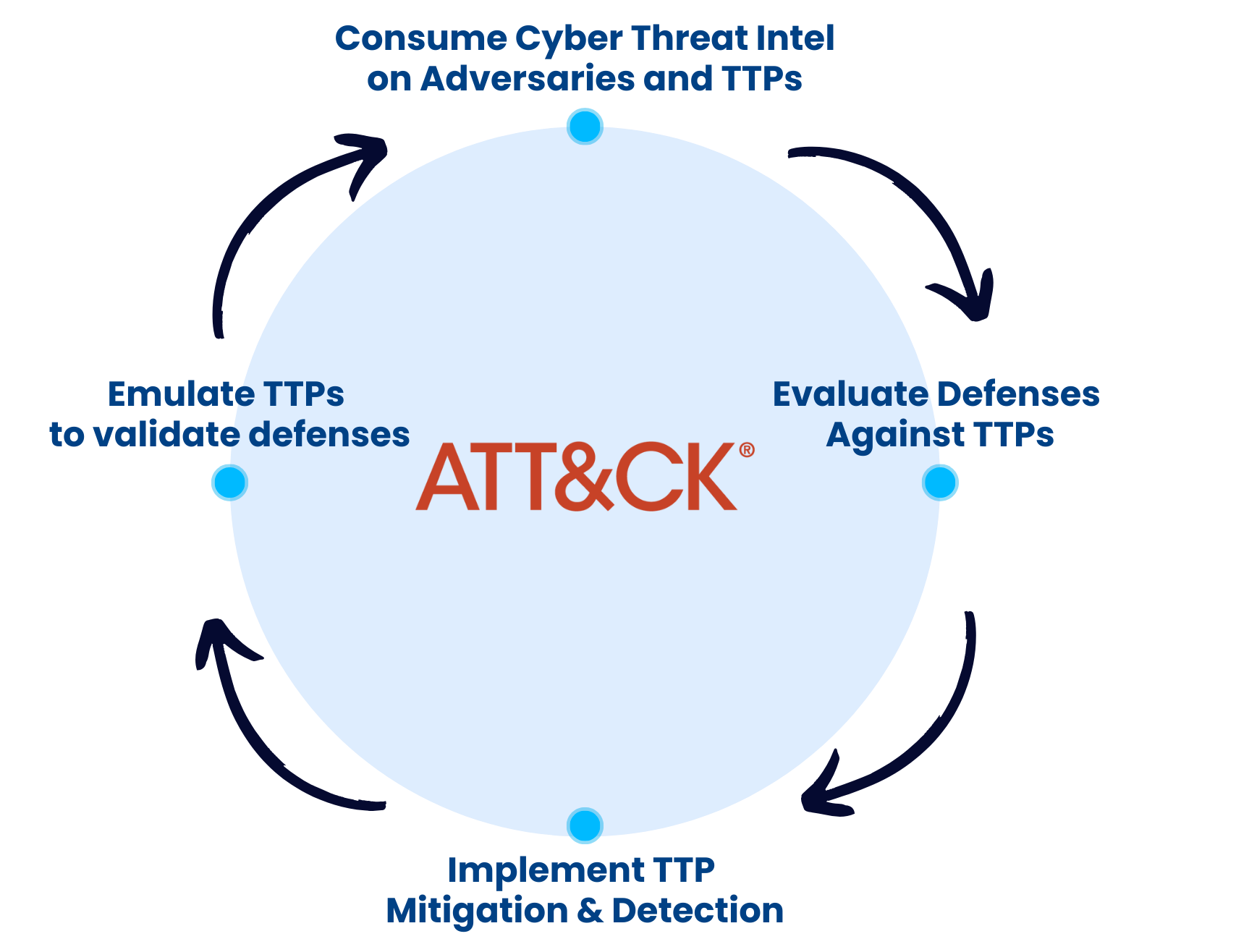
Threat-informed defense is not a tool or tactic but a methodology; at the heart of it is MITRE ATT&CK, the curated knowledge base and model for cyber adversary behaviour. A repository that weaves the cyber threat information, vulnerabilities, mitigations, recommendations, and detection strategies into classes known as TTPs.
Accelerate Security Posture Improvement
Talking about adversary emulation, simulation, or purple team is critical to the Threat-informed Defense cycle. Threat-informed Defense is about using threat intelligence and how we can test and evaluate our systems and defenses, identifying and filling the gaps in prevention and detection.
Purple teaming enables collaboration and becomes a practical component of threat-informed defenses. At the same time, adversary emulation helps generate actionable evidence of prevention and detection for the intelligence, red and blue teams.
Solutions and vendors will always talk about stopping every threat out there, and it's just a promise, not evidence. But applying threat-informed defense principles, adversary emulation, and purple teaming can move things out of the land of promise to a ground of evidence-based security.
FourCore enables Threat-Informed Defense by helping organisations better understand adversaries and their TTPs with Adversary Emulation, helping them operationalise threat intelligence by providing the capability to assess their organisations against the latest threats that matter to them and promote collaboration between the security teams via Purple Teaming.

Emulating threats with FourCore ATTACK
Learn about the latest ransomware groups and how emulate threats in a most realistic manner on the FourCore blog.
Meet the FourCore team and get a demo of the FourCore ATTACK platform here.
- Clop Ransomware: History, Timeline, And Adversary Simulation
- Exploit Party: Bring Your Own Vulnerable Driver Attacks
- Ryuk Ransomware: History, Timeline, And Adversary Simulation
- ATT&CK + D3FEND = D.E.A.T.H
- A Malicious Note: Hackers Using Microsoft OneNote Attachments To Spread Malware
- EDR: Detections, Bypassess And Other Shenanigans
