Last Updated on Sun Jan 29, 2023
A Malicious Note: Hackers using Microsoft OneNote Attachments to spread malware

Hackers are using Microsoft OneNote attachments in phishing emails to spread malware and password stealers. Phishing Campaigns is one of the most typical ways hackers obtain private or sensitive information. Phishing involves sending fraudulent emails that appear to come from a trusted source. Its purpose is to trick recipients into clicking on a malicious link or downloading a malicious file, usually to steal money or personal information. According to a report by Verizon, 94% of the malware is delivered by email.
Malicious Word and Excel attachments for phishing have been prevalent for a long time, known to compromise recepients using macros to download and install malware. However, in July 2022, Microsoft blocked Macros by default on all Office applications, making this approach unreliable for spreading malware. Since then, hackers have come up with various modern email-based initial access vectors. We discussed some of these new techniques in New Era Of Phishing Payloads. Examples include using .iso and .zip container files to deliver malicious payloads.
In this post, we'll look at how hackers are now using OneNote attachments in phishing emails to spread malware and password stealers to their victims.
How OneNote Malware works?
TL;DR: To summarize, Microsoft OneNote allows user to embed files in a notebook. An attacker can deceit a user into clicking a file which can act as a dropper to download and execute the malicious payload. Hackers have been embedding different payloads such as .wsf, .exe, .vbs, other executable and script formats to execute malicious code on a recepient's system. That's it.
The Detailed Version
Integrated into Microsoft Office 2019 and Microsoft 365, Microsoft OneNote is a desktop digital notebook application that can be downloaded for free. Even if a Windows user isn't using Microsoft OneNote, the application is still present to open the file format since it comes pre-installed with all Microsoft Office/365 installations.
According to reports by Trustwave Spiderlabs, since December 2022, malicious spam emails with OneNote attachments had begun to be distributed by hackers primarily containing Formbook and Agent Tesla payloads.
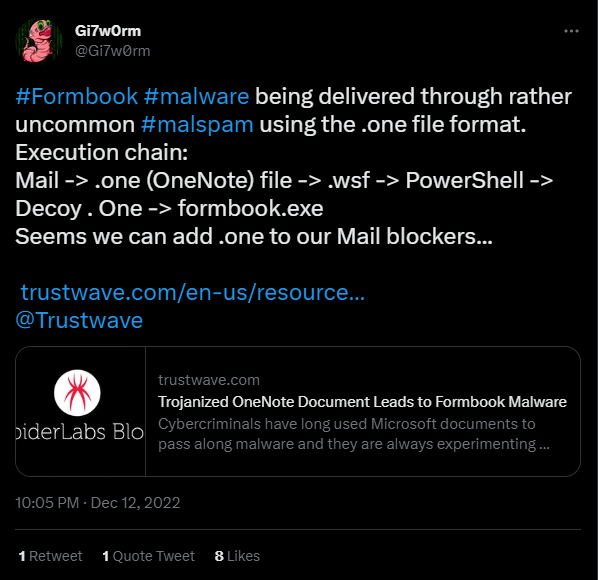
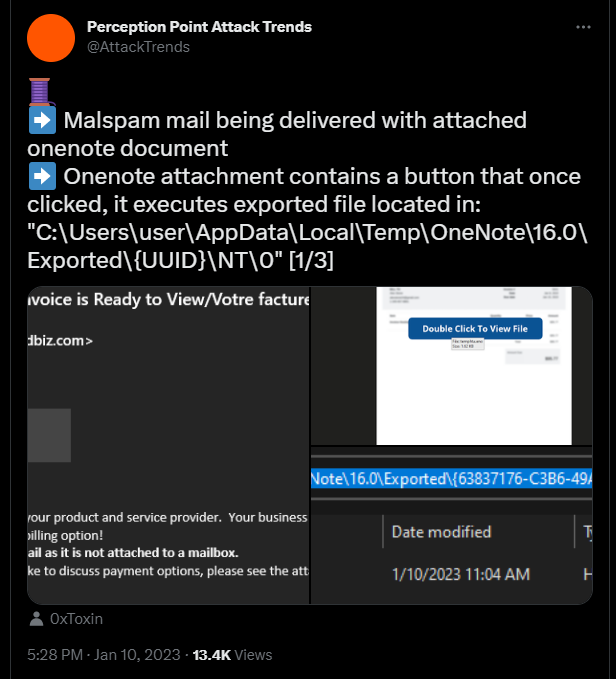
It is essential to note that Microsoft OneNote itself doesn't support macros like its senior partners Word and Excel.
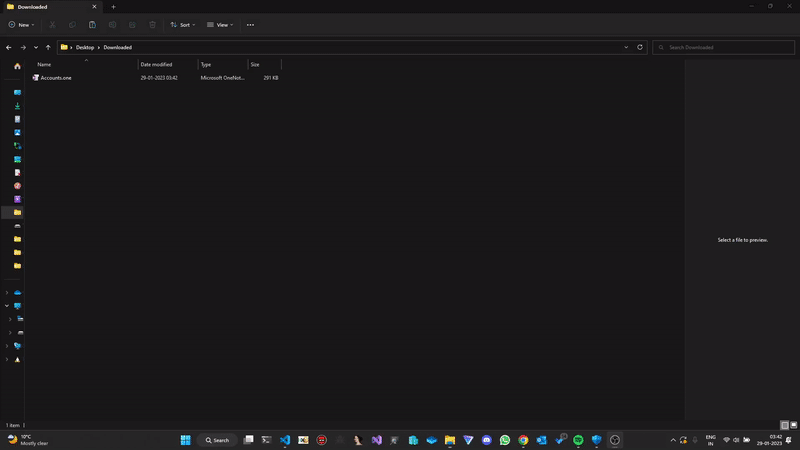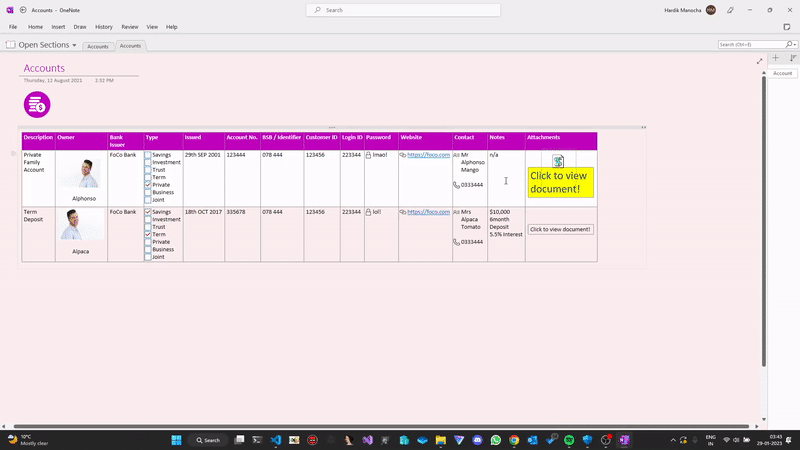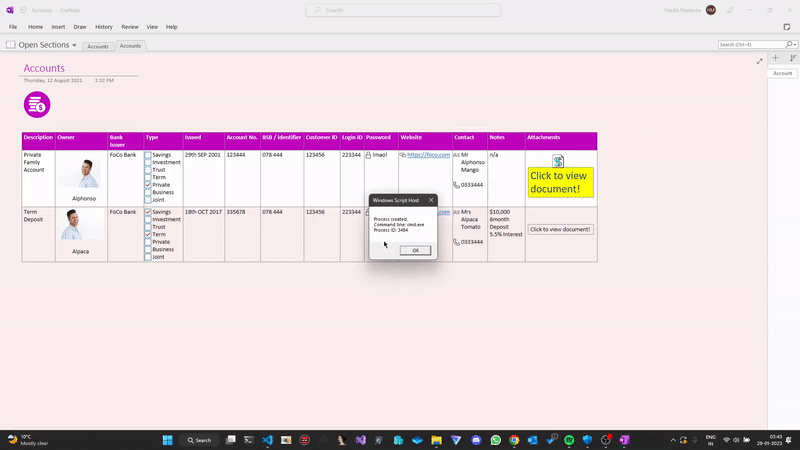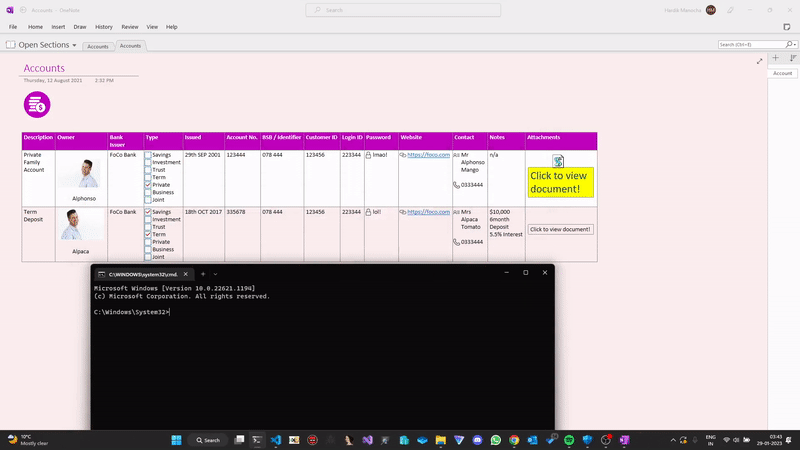
These malicious OneNote documents are sent out as attachments with phishing emails like invoices, ACH transfer forms, DHL delivery emails, and other documentation. A malicious attachment masquerading as a "notebook" is downloaded together with the OneNote file when the target victim downloads it. Threat actors overlay the notebook with a "Click to view content" or "Double click to view document" banner trick the recepient into loading the attachment. The computer will warn you when you click about the risks of opening attachments which might harm your system or data. However, users typically ignore these, and if they select "OK," the script would download and install a RAT from the C2 servers.
One excerpt from ThreatPost's Analysis on Agent Tesla Ransomware:
The various OneNote versions had different lures as well. One told victims that a transfer had been successfully received from their bank invoice and told them to click on a link to view the details of the transfer (which actually downloaded malware), while another told them that their OneDrive isn’t synced with their organization’s backup, and asked them to “auto verify” in order to fix the issue — which brought them to a phishing page.
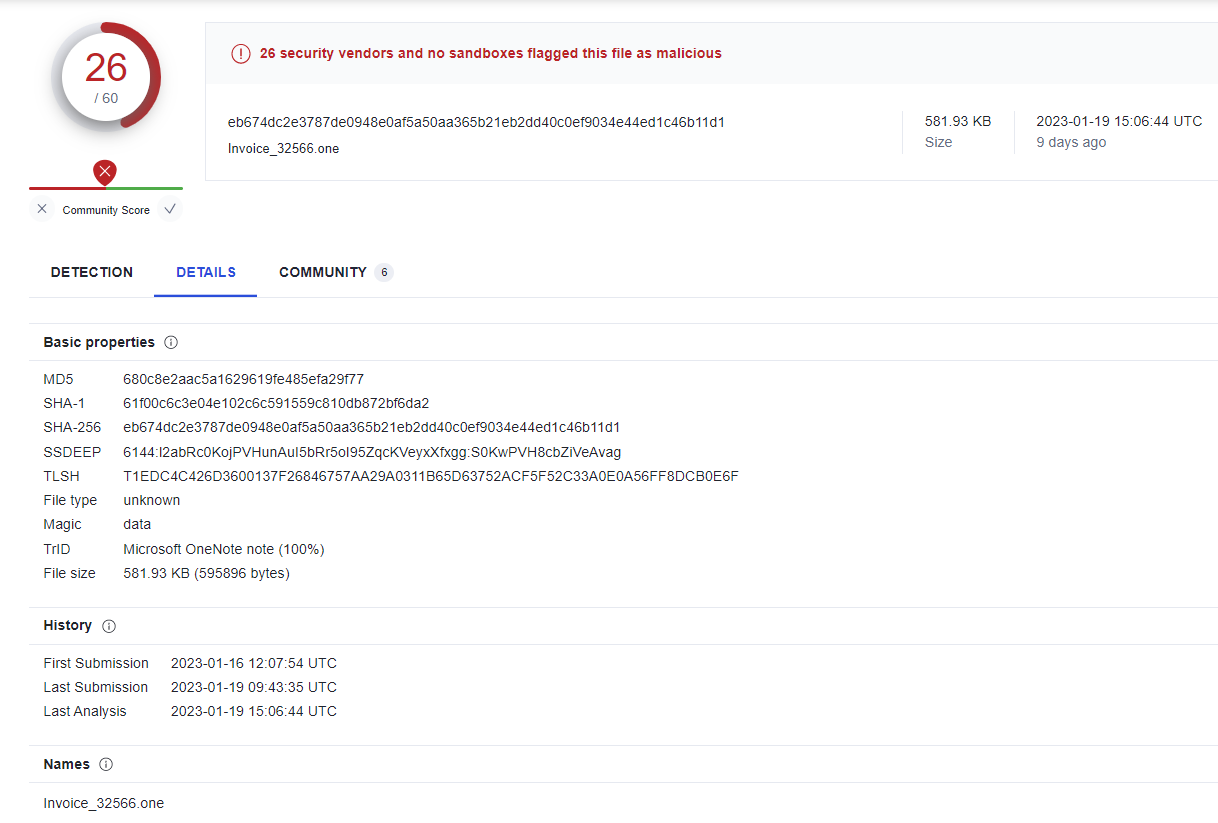
A VirusTotal sample of one such attachment:
Here's the complete execution flow:
- A user is lured into downloading and opening a OneNote attachment.
- Upon opening, the user is deceived by a possible button to open a report/document.
- A warning is presented in front of the user; to block the execution, the user can select "Cancel".
- If selected "OK", the attached payload is executed, which generally acts as a downloader for the primary payload.
How to protect against such threats?
Every enterprise is strongly advised to keep its employees informed of the latest phishing campaigns employed by malicious attackers. In addition, keeping on top of your system updates and always using the newest version of technology from Microsoft is essential when you want to keep your business safe. Beyond user awareness, file-based and behavioural detections can be deployed for the malicious OneNote files.
Yara Rules
- gen_onenote_phish.yar
- Detects suspicious OneNote attachments containing embedded files.
Sigma Rules
- OneNote Attachment File Dropped In Suspicious Location
- Detect the creation of a
.onefile typically used in such campaigns.
- Detect the creation of a
Assess, Validate and Remediate
Ideally, .one should be blocked at the perimeter or the email gateway.
However, one must also assess whether the installed rules and filters are working as expected. This allows you to validate your controls against such attacks and ensure you can timely respond to these threats.
We have deployed safe email attack simulations containing malicious and benign OneNote Attachments in the FourCore ATTACK platform to validate your email security simulations against OneNote malware.
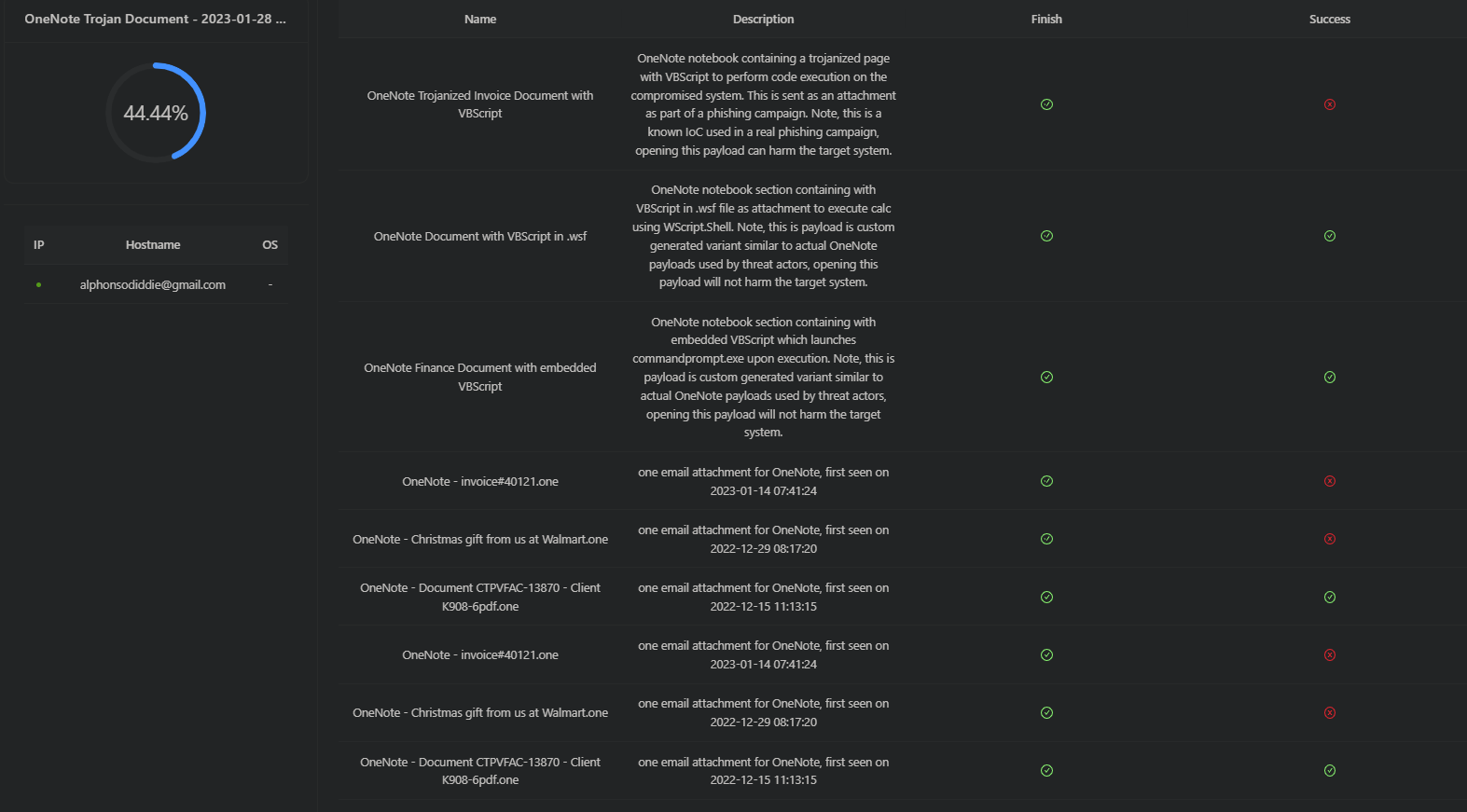
An exciting find 😉when assessed against O365 and Gsuite. Learn more at @FourCore.
References
