Last Updated on Sun Jan 08, 2023
Exploit Party: Bring Your Own Vulnerable Driver Attacks

BYOVD or Bring Your Own Vulnerable Driver is an attack where a threat actor brings a legitimately signed and vulnerable driver to perform malicious actions on the system. In a BYOVD attack, the attacker can use the vulnerabilities in the driver to execute malicious actions with kernel-level privileges!
In this post, we’ll understand how BYOVD attacks work, how vulnerable drivers have been exploited by threat actors such as the Cuba Ransomware Group and Lazarus Group and what we can do to prevent these attacks. (and bonus at the end!)
What is a Driver?
Drivers are software that acts as an intermediary between the operating system and a Device. A driver translates the operating system's instructions into actions that the device can understand and carry out. Without a driver, a computer would not be able to use the various connected devices.
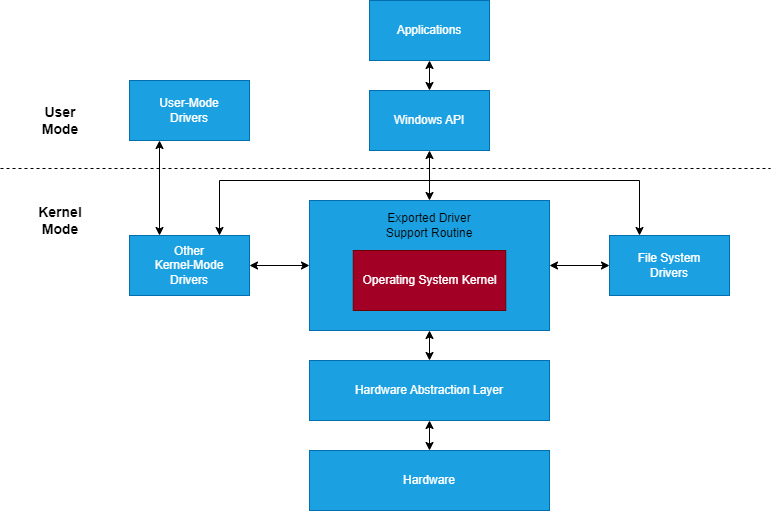
Communication between User Mode and Kernel Mode
Drivers are also developed to provide support for software applications or functions within the operating system that are not natively present in the operating system. An example is a File System driver, which can allow access to different types of filesystems(ExFat, Ext4), which the OS does not natively support. Just like any software, a driver can have vulnerabilities. Attackers exploit these vulnerabilities to gain kernel privileges during an attack known as a Bring Your Own Vulnerable Driver (BYOVD) attack.
APTs adopt Vulnerable Drivers
Various different APTs and Threat actors have been adopting vulnerable drivers to bypass security controls and establish a deeper foothold into the system. Since the drivers are cross-signed by Microsoft, they are inherently trusted by security solutions. Moreover, since the drivers run with kernel-level privileges, even behaviour-based detections can be bypassed.
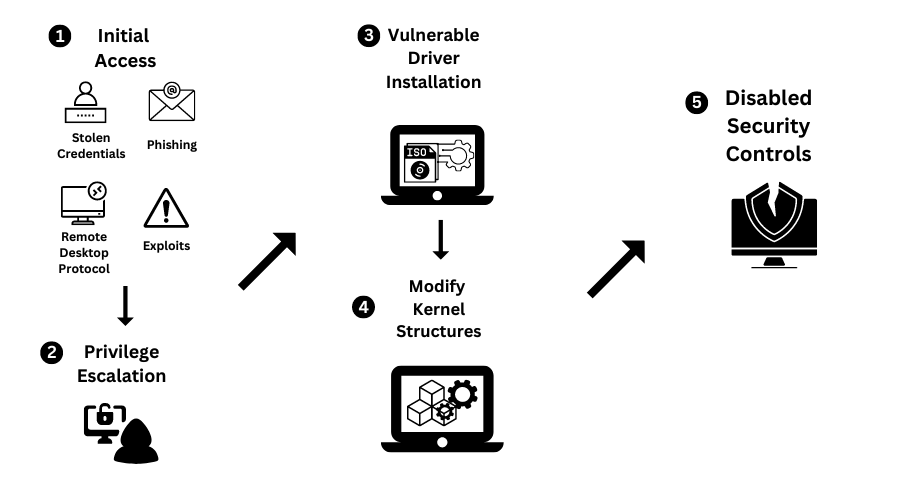
The first ever recorded abuse of vulnerable drivers was by the Lazarus group in 2021, where they used the Dell vulnerable driver to disable seven monitoring sources provided by Windows. Using improper access control and kernel read-write primitive vulnerabilities, the attackers disabled monitoring of various events such as registry, file system, process creation, etc. This blinded any security software running on the system leading to organizations having a false sense of security.
Another example is the Avast Vulnerable Driver used by the Cuba Ransomware group. The Vulnerable driver allows any user to kill processes with kernel-level privileges. This capability allowed the ransomware operators to escalate their privileges and kill protected processes such as security software without authorization.
There are many open-source PoCs to showcase the exploitation of these vulnerable drivers to bypass protections. An example is the dellicious project which uses the Dell Vulnerable driver to disable PPL protection on the lsass.exe process.
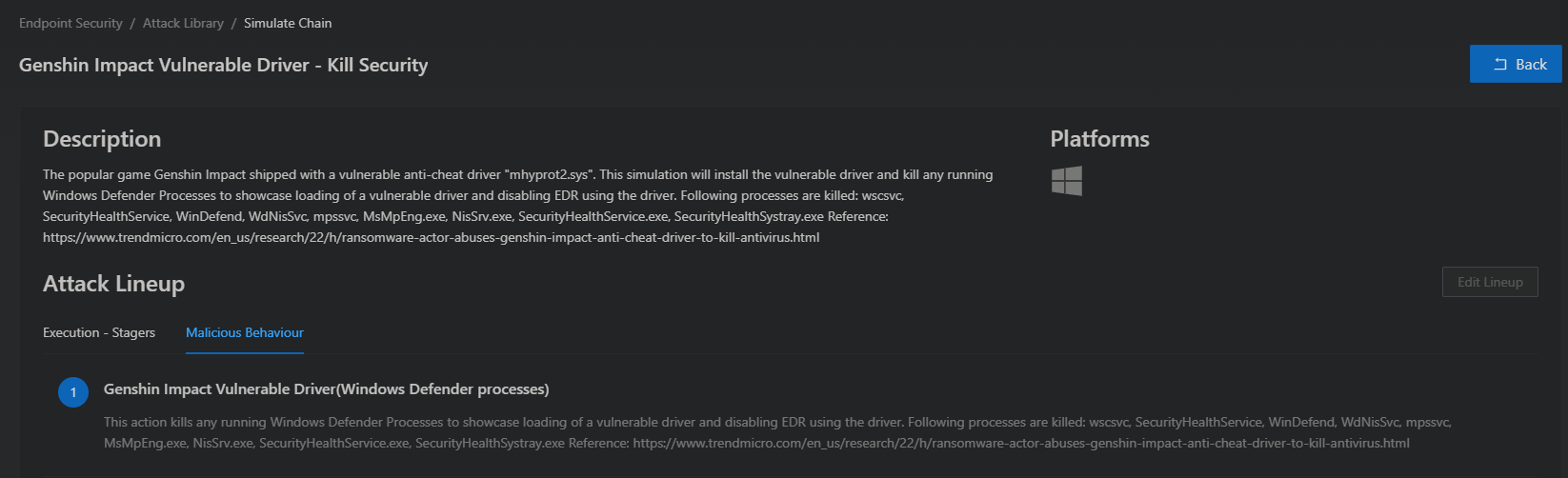
Another example is the mhyprot project which utilizes a vulnerable version of the Genshin Impact anti-cheat to provide arbitrary read-write to the kernel memory.
An open-source project called Kernel Cactus has also converted the Dell vulnerable driver as a library which can be used for Handle Elevation, Token Stealing, PPL toggling, and many other security control bypasses. Projects such as these provide capabilities in the hands of attackers and defenders alike, and it is essential to update your threat model to incorporate BYOVD attacks.
Drivers and Kernel Memory
The kernel is the heart of the operating system, which completely controls the hardware and software of the device.
The kernel is loaded into a separate protected region in the memory and is protected from access by other non-critical parts of the OS (or malware, you know). Access to the functionalities of the kernel from user-mode applications is only allowed via specific APIs called system calls or drivers (via IOCTLs).
Applications running in user mode have fewer privileges to control the system. They can only access a virtualized view of memory which is isolated and protected from the rest of the system. On the other hand, a driver runs inside kernel memory and can perform any operation just like the kernel. A driver can access and modify critical security structures. These modifications can lead to attacks such as Privilege Escalation, Arbitrary Read-Write and disabling of security services responsible for the protection of the Operating System.
How to prevent Bring Your Own Vulnerable Driver Attacks
To prevent these attacks, you can focus on blocking IoCs (such as driver file hashes) relevant to known vulnerable drivers. Updating the driver block list present on Windows with the latest threat intelligence and IoCs.
It is necessary to understand that these methods only protect against known vulnerable drivers, and attackers can discover new vulnerable drivers unknown to the community.
Driver Signature Enforcement
To protect against such attacks, Operating Systems have mitigations such as Driver Signature Enforcement, which only allows drivers cross-signed by Microsoft to load on the system. This ensures that in case any vulnerability or malicious use is discovered, the signature can be revoked and prevent exploitation of the system.
Microsoft also maintains driver block rules to protect against known vulnerable drivers. Microsoft also recommends turning on Hypervisor Protected Code Integrity or HVCI to protect against vulnerable drivers.
Assess, Validate and Remediate
BYOVD attacks are going to increase in number in coming years. As the security software moves more towards the kernel with protections like EtwTi, attackers are also moving towards the kernel to bypass these security controls.
It’s vital to assess if you are protected against Bring Your Own Vulnerable Driver Attacks, validate your controls against such attacks, and ensure you can timely respond to these threats. You can safely simulate BYOVD attacks on your own infrastructure with the FourCore ATTACK platform.
We have developed automated simulations for BYOVD attacks used by threat actors such as the Cuba Ransomware Group or exploiting a vulnerable version of the Genshin Impact driver to kill security controls on your system.
References
Cuba Ransomware utilizing Avast vulnerable driver
